Master RemoteIoT SSH On AWS: Your Ultimate Guide
Are you ready to unlock the full potential of your Internet of Things (IoT) projects by harnessing the power of Amazon Web Services (AWS)? The fusion of RemoteIoT, Secure Shell (SSH), and AWS offers a pathway to secure, scalable, and efficient IoT management.
Imagine a world where your IoT devices, spread across geographical boundaries, are managed with ease and security. This is the promise of AWS, a robust platform offering a suite of services designed to facilitate secure communication and data processing. The RemoteIoT SSH AWS Example acts as your compass, guiding you through the intricacies of establishing and maintaining secure SSH connections on AWS for your IoT endeavors. This comprehensive guide is crafted for both seasoned developers and those just beginning their IoT journey, offering invaluable insights and practical applications to elevate your projects.
This guide will unravel the complexities of integrating IoT with AWS, ensuring you possess the knowledge and tools needed to build robust, secure, and scalable solutions.
- Lakers Roster 2023 Analysis Game Highlights
- Temporary Replacement Parts Your Essential Guide Amp Faqs
- Introduction to RemoteIoT SSH AWS Example
- Understanding IoT Basics
- AWS Overview
- What is SSH?
- Setting Up RemoteIoT
- AWS SSH Setup
- Example Implementation
- Security Best Practices
- Troubleshooting Tips
Introduction to RemoteIoT SSH AWS Example
At its core, the RemoteIoT SSH AWS Example provides a blueprint for the secure and efficient management of IoT devices using AWS's comprehensive infrastructure. SSH, or Secure Shell, is the critical protocol that establishes encrypted connections between your devices and the cloud. AWS, in turn, provides the ideal platform to scale these connections, ensuring your IoT projects are both secure and capable of handling increasing demands.
This exploration will delve into the essential role of SSH in IoT projects and how AWS simplifies the complex process. It will lay the groundwork for the subsequent sections, preparing you to embark on this exciting technological journey. Let's get started!
Understanding IoT Basics
What is IoT?
The Internet of Things (IoT) represents a vast network of interconnected physical devices, each equipped with sensors, software, and connectivity, allowing them to exchange data. These devices range from everyday smart home appliances to sophisticated industrial machinery, all designed to enhance efficiency, automation, and convenience.
- Remote Update Raspberry Pi Download The Ultimate Guide
- Lara Rose The Complete Guide Why She Matters Now
Key benefits of IoT include:
- Increased automation
- Improved data collection and analysis
- Enhanced user experience
Why IoT Matters in 2023
As the world becomes increasingly interconnected, IoT continues to play a vital role in various industries. From healthcare to manufacturing, IoT solutions are transforming the way businesses operate. Grasping the fundamentals of IoT is crucial for anyone looking to leverage its potential.
AWS Overview
What is AWS?
Amazon Web Services (AWS) is a comprehensive cloud platform providing an extensive array of services. These include computing power, versatile storage options, and sophisticated database management solutions. AWS is recognized for its scalability, reliability, and robust security features, making it the preferred choice for many technology enthusiasts.
Some key AWS services include:
- EC2 (Elastic Compute Cloud)
- S3 (Simple Storage Service)
- RDS (Relational Database Service)
Why Choose AWS for IoT?
AWS offers seamless integration of IoT services, ensuring your devices are easily connected, managed, and secured. With features such as AWS IoT Core and AWS Lambda, you can design scalable and efficient IoT solutions tailored to your precise needs. AWS provides an ecosystem to manage and process data, offering significant advantages in terms of scalability, security, and cost-effectiveness.
What is SSH?
SSH Basics
Secure Shell (SSH) is a cryptographic network protocol, designed to secure communication between devices over an unsecured network. It is extensively used for remote system administration, secure file transfers, and providing a safe way to access servers and other devices.
Key features of SSH include:
- Encryption
- Authentication
- Secure data transfer
Why Use SSH for IoT?
SSH is essential for IoT projects, guaranteeing secure communication between devices and the cloud. By using SSH, you can protect sensitive data and uphold the integrity of your IoT ecosystem. It is a must-have tool for anyone serious about IoT security. SSH provides a secure channel for remote access, command execution, and data transfer, ensuring that sensitive information remains confidential and protected from unauthorized access.
Setting Up RemoteIoT
Step-by-Step Guide
Setting up RemoteIoT involves a series of steps, from device configuration to establishing secure connections. Here is a concise guide to get you started:
- Install necessary software on your IoT devices.
- Configure network settings for optimal performance.
- Set up SSH keys for secure authentication.
Each step is crucial for preparing your IoT devices to connect to AWS. Carefully consider each configuration, as it forms the foundation for a successful setup.
Consider this table for a comprehensive overview of the key steps involved in setting up RemoteIoT. This table offers a structured approach, enhancing clarity and usability:
| Step | Description | Action | Considerations |
|---|---|---|---|
| 1. Software Installation | Install necessary software components like the SSH client/server and any device-specific drivers. | Use package managers (e.g., apt, yum) or manual installation methods. | Ensure compatibility with your device's operating system. |
| 2. Network Configuration | Configure network settings such as IP addresses, DNS servers, and gateway addresses. | Configure either static or dynamic IP assignments. | Ensure proper network connectivity, including firewall settings. |
| 3. SSH Key Setup | Generate and configure SSH keys for secure authentication. | Generate key pairs (private/public) and distribute the public key to the remote device. | Prioritize strong key types (e.g., RSA 4096-bit) and security protocols. |
| 4. SSH Server Configuration | Configure SSH server settings on the IoT devices. | Modify SSH configuration files (e.g., sshd_config) to enable key-based authentication and disable password authentication. | Regularly update your SSH server to address any security vulnerabilities. |
| 5. AWS EC2 Instance Setup | Create an EC2 instance and configure network settings to ensure your IoT devices can reach the instance via SSH. | Configure security groups to allow SSH access from your IoT devices. | Set up a static IP address or a DNS name for the EC2 instance for ease of access. |
| 6. Establish SSH Connection | Establish SSH connections from your IoT devices to the AWS EC2 instance. | Use the SSH command-line tool or a GUI client to connect. | Verify the connection by running a simple command. |
For further details and in-depth tutorials, explore official AWS documentation and community forums.
Reference: AWS Documentation
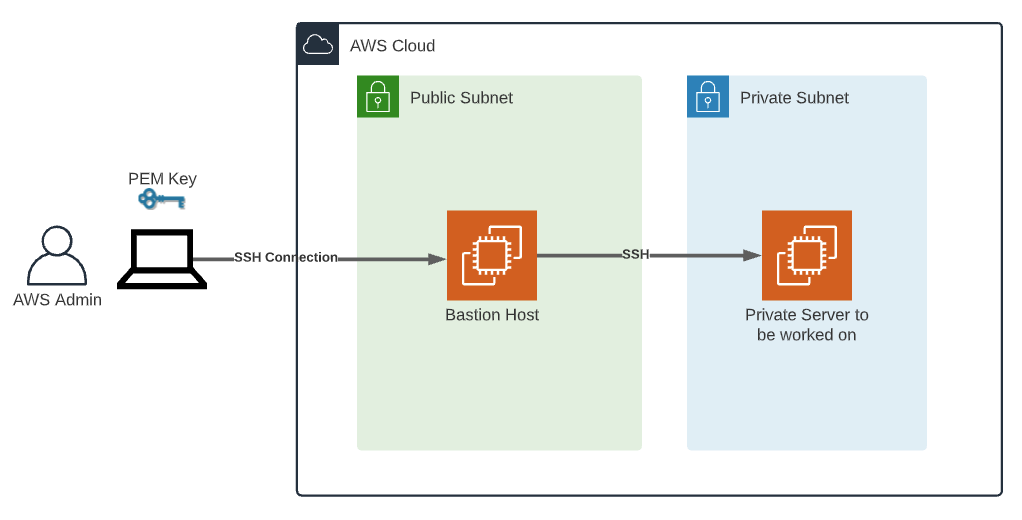
AWS SSH Setup
Connecting IoT Devices to AWS
Establishing a secure connection between your IoT devices and AWS via SSH is a streamlined process. The steps below will guide you through the setup:
- Create an EC2 instance on AWS.
- Generate SSH keys for secure access.
- Connect your IoT devices to the EC2 instance using SSH.
By following these steps, you will establish a secure and scalable connection between your IoT devices and AWS. This setup forms the backbone of your RemoteIoT SSH AWS Example.
Here's a table that simplifies the steps to connect your IoT devices to AWS via SSH. This structured approach breaks down the process into manageable components:
| Action | Description | Considerations |
|---|---|---|
| Create an EC2 Instance | Launch an EC2 instance with an appropriate operating system (e.g., Ubuntu, Amazon Linux). | Choose an instance type that suits your needs (e.g., t2.micro for testing). |
| Generate SSH Keys | Create a key pair (public and private key) when launching the EC2 instance or generate one locally. | Store your private key securely (do not share it). |
| Configure Security Group | Configure the security group associated with the EC2 instance to allow SSH traffic (port 22) from your IoT devices' IP addresses or a specific range. | Restrict the security group's inbound rules to only allow necessary traffic. |
| Connect IoT Devices to EC2 | Use the public IP address or DNS of the EC2 instance and the private key file to connect to the instance via SSH. | Ensure your IoT devices have an SSH client installed. |
| Test Connection | Once connected, test the connection by running a simple command (e.g., `ls`). | Verify that your IoT devices can successfully execute commands on the EC2 instance. |
For more specific, tailored solutions, and troubleshooting strategies, turn to the official AWS documentation or consult with AWS specialists.
Reference: Amazon EC2
Example Implementation
A Practical Example
Let's examine a practical application of the RemoteIoT SSH AWS Example. Consider a scenario where you have a network of IoT sensors monitoring environmental conditions. Below is a breakdown of how to set up such a system:
- Deploy your sensors with SSH capabilities.
- Set up an EC2 instance on AWS to collect data.
- Use SSH to securely transfer data from sensors to the EC2 instance.
This example highlights the capabilities of integrating IoT with AWS, enabling you to collect and analyze real-time data effectively.
Here is a tabular demonstration of a real-world example, enabling structured understanding:
| Component | Function | Technology |
|---|---|---|
| IoT Sensors | Measure environmental conditions (temperature, humidity, pressure, etc.). | Arduino, Raspberry Pi, ESP32 |
| SSH Client | Enables secure data transfer from sensors. | OpenSSH, Dropbear |
| Data Transfer Protocol | Mechanism for securely uploading sensor data. | SSH using `scp` or `rsync` |
| EC2 Instance | Collects, stores, and processes the data from sensors. | AWS EC2 (e.g., Ubuntu) |
| Data Storage | Stores the collected sensor data. | AWS S3, AWS DynamoDB, PostgreSQL |
| Data Analysis & Visualization | Processes data for analytics and generates real-time visualizations. | AWS Lambda, AWS CloudWatch, Grafana |
This table helps visualize how the distinct components come together to accomplish a useful purpose. Consider using a variety of resources to enhance your learning. For more details, look at AWS documentation and community forums.
Reference: AWS IoT Core
Security Best Practices
Securing Your IoT Devices
Security is of utmost importance in IoT projects. The following are some key practices to ensure the safety of your devices and data:
- Use strong, unique SSH keys.
- Regularly update firmware and software.
- Monitor network activity for suspicious behavior.
Adhering to these practices will safeguard your IoT ecosystem against potential threats, securing its integrity and resilience.
Here's a table that outlines security best practices in an actionable manner:
| Best Practice | Description | Implementation |
|---|---|---|
| Strong SSH Keys | Use lengthy, unique SSH keys (RSA 4096-bit or higher). | Generate strong keys, rotate regularly, and protect your private key. |
| Regular Software Updates | Regularly update the firmware and software on your devices. | Set up automated update processes or schedule updates. |
| Network Monitoring | Monitor network traffic for anomalous behavior. | Implement intrusion detection systems. |
| Firewall Configuration | Restrict network access using firewalls. | Configure firewalls to allow only necessary traffic to and from your devices. |
| Access Control | Limit access to your devices. | Implement strong authentication, access control lists, and multi-factor authentication. |
| Data Encryption | Encrypt all data in transit and at rest. | Use SSH, HTTPS, and encryption algorithms. |
By applying these practices, you are setting the foundation for a secure IoT environment. For more insight, refer to security guides and specialized resources.
Reference: OWASP (Open Web Application Security Project)
Troubleshooting Tips
Common Issues and Solutions
Even with a well-designed setup, encountering issues is possible. Here are solutions to common problems:
- Connection errors: Investigate network configurations and SSH setups.
- Data transfer issues: Confirm permissions and firewall settings.
- Device malfunctions: Restart devices and confirm software updates.
These tips will assist you in quickly resolving issues, keeping your IoT projects functioning seamlessly.
Here's a table to assist you in troubleshooting and provide specific remedies:
| Issue | Possible Cause | Solution |
|---|---|---|
| Connection Errors | Incorrect IP address, port issues, firewall restrictions. | Verify IP addresses, test port connectivity using `telnet` or `nc`, and check firewall rules. |
| Authentication Failures | Incorrect username, password, or SSH key problems. | Double-check credentials, verify key permissions, and ensure the SSH server allows key-based authentication. |
| Data Transfer Problems | File permissions, incorrect path, insufficient disk space. | Examine file permissions, ensure the correct paths, and check disk space on the device. |
| Device Malfunctions | Software bugs, hardware failure, connectivity problems. | Reboot the device, ensure software is updated, and check for hardware issues. |
| Firewall Issues | Firewall blocking SSH connections. | Check firewall settings, and ensure SSH (port 22) is allowed. |
Through consistent troubleshooting, you will improve your IoT projects. Utilize community resources for detailed answers.
Reference: Server Fault


Detail Author:
- Name : Prof. Gerhard Romaguera
- Username : myrtle.stiedemann
- Email : broderick.langosh@borer.com
- Birthdate : 1993-09-29
- Address : 260 Lueilwitz Burgs Suite 999 Jaleelton, MS 55517
- Phone : 915.264.7620
- Company : Wintheiser PLC
- Job : Tractor Operator
- Bio : Delectus ex nesciunt voluptatibus temporibus eius. Omnis et atque enim sit. Sequi soluta eum sunt iure voluptatem exercitationem rem. Provident laboriosam sed ea praesentium neque.
Socials
twitter:
- url : https://twitter.com/turner1999
- username : turner1999
- bio : Et quis voluptatibus molestiae. Minima nesciunt ratione totam quaerat. Enim qui quas vel enim.
- followers : 4310
- following : 222
instagram:
- url : https://instagram.com/audraturner
- username : audraturner
- bio : Aperiam repellendus dolorem sit perferendis. Et inventore omnis amet quis dolore.
- followers : 3430
- following : 505