RemoteIoT VPC: A Beginner's Guide To Securing Your IoT Devices
Curious about how to create a secure and efficient ecosystem for your Internet of Things (IoT) devices in the cloud? RemoteIoT VPC is the key, and understanding its intricacies can significantly elevate your projects.
Managing IoT devices remotely can indeed be a complex undertaking, often evolving into a series of challenges. The need for a robust, secure, and scalable infrastructure becomes paramount as the number of interconnected devices continues to rise exponentially. RemoteIoT VPC emerges as a pivotal solution. Its essentially a digital stronghold, engineered to provide the necessary layers of security and isolation that your IoT projects demand. By adopting this technology, one can successfully create a secure, isolated network where devices communicate flawlessly, all while remaining impervious to potential security threats.
Table of Contents
- What is RemoteIoT VPC?
- Why Use RemoteIoT VPC?
- Setting Up RemoteIoT VPC
- Security Best Practices
- Benefits of RemoteIoT VPC
- Troubleshooting Tips
- Real-World Applications
- Common Pitfalls to Avoid
- Optimizing Performance
What is RemoteIoT VPC?
Let's delve into the fundamentals. RemoteIoT VPC, or "Virtual Private Cloud," is essentially a customized, private cloud environment designed specifically for IoT deployments. Think of it as a private, secure network residing within the broader cloud infrastructure, serving as the home for your IoT devices. This specific setup guarantees that devices are shielded from external threats while maintaining the capacity to communicate both internally and with your cloud-based resources. The primary objective here is to provide a secure and efficient operational environment.
The core principle behind RemoteIoT VPC is isolation. It establishes a clearly defined perimeter around your IoT devices, protecting them from potential security breaches and malicious attacks. In addition, it offers a way to efficiently manage these devices by organizing them into logical subnets, assigning unique IP addresses, and setting up sophisticated access controls. It is comparable to having a specialized IT administrator dedicated to your IoT projects.
Key Features of RemoteIoT VPC
- Isolated network environment for IoT devices.
- Flexible subnet configuration for better organization.
- Advanced security features to protect your devices.
- Easy integration with other cloud services.
Why Use RemoteIoT VPC?
Given the definition, the next logical question is: why adopt RemoteIoT VPC? The proliferation of IoT devices and the massive data streams they generate necessitate robust management strategies. The secure and efficient handling of this data is far from trivial. This is where RemoteIoT VPC truly shines, delivering a comprehensive solution.
By using RemoteIoT VPC, you can gain several critical advantages:
- Enhance security by isolating your devices from the public internet.
- Improve performance by optimizing network configurations.
- Reduce costs by efficiently managing resources.
- Scale your IoT projects effortlessly as your needs grow.
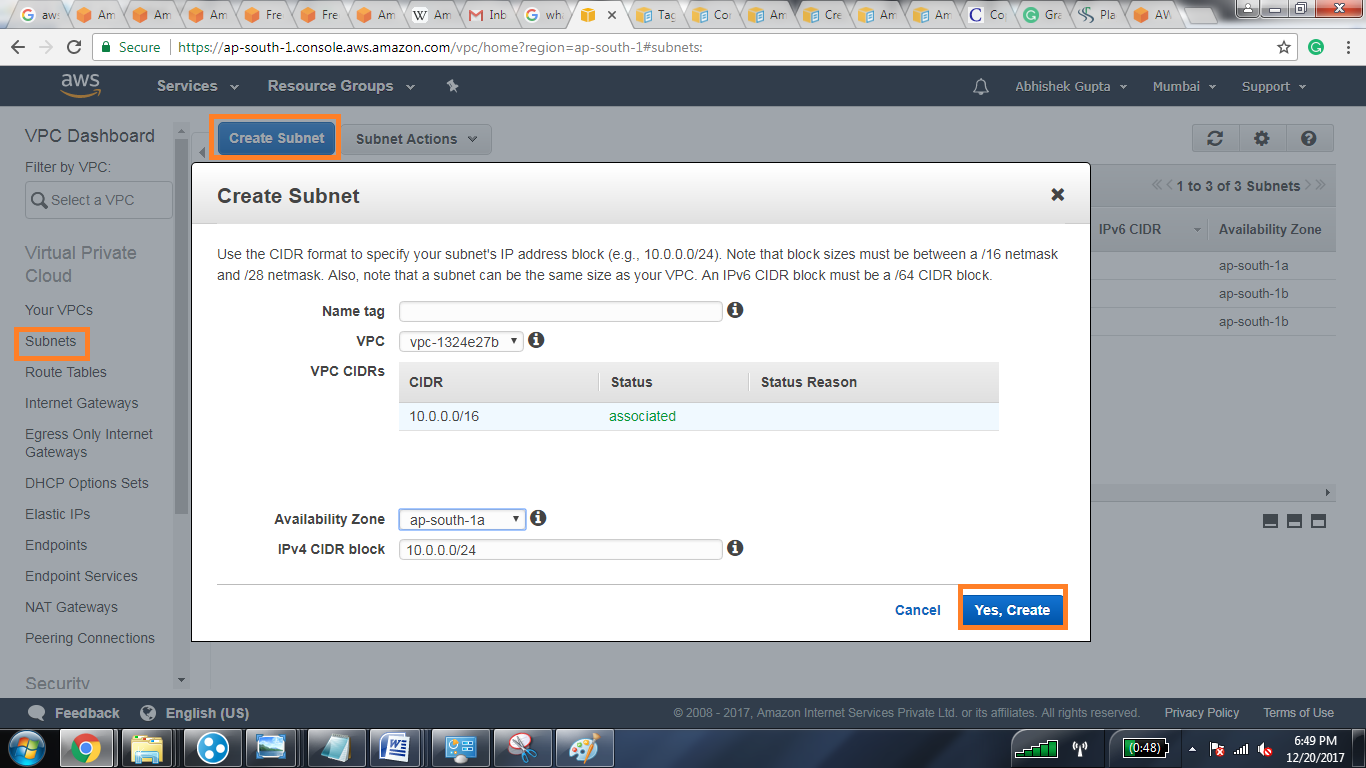
Setting Up RemoteIoT VPC
Setting up RemoteIoT VPC might seem complex initially, but in reality, the process is quite manageable. A step-by-step guide can help simplify the initial setup:
Step 1
The initial step involves creating a new VPC. This is where your IoT devices will reside. It's essential to select a CIDR block that accommodates your specific needs, with 10.0.0.0/16 often being a suitable choice.
Step 2
Once the VPC is created, the next step is to configure subnets. Subnets act as smaller networks within the larger VPC, facilitating organization based on device functions or locations. For example, you could create a subnet exclusively for sensors and another for actuators.
Step 3
Security groups function as firewalls within your VPC, controlling incoming and outgoing traffic for your devices. Careful configuration is critical to ensure that only authorized traffic can pass through.
Security Best Practices
Security should always be a priority when using RemoteIoT VPC. Here are some key best practices to secure your devices:
- Use strong passwords and encryption for all your devices.
- Regularly update your firmware and software to patch vulnerabilities.
- Monitor your network for suspicious activity using intrusion detection systems.
- Limit access to your VPC to only those who need it.
Benefits of RemoteIoT VPC
What tangible advantages does RemoteIoT VPC offer? A multitude of benefits can be reaped. Here are a few:
- Enhanced security for your IoT devices.
- Improved performance through optimized network configurations.
- Scalability to grow with your IoT projects.
- Cost savings through efficient resource management.
Troubleshooting Tips
Even with a well-configured setup, issues can arise. Here are some troubleshooting tips to help navigate any challenges:
- Check your security group rules to ensure they’re allowing the right traffic.
- Verify your subnet configurations to make sure devices are in the right network.
- Review your VPC settings to ensure everything is set up correctly.
Real-World Applications
RemoteIoT VPC is more than just a theoretical concept; it's actively utilized in real-world applications. Here are some examples:
- Smart cities using IoT devices to monitor traffic and energy usage.
- Industrial IoT applications for monitoring and controlling machinery.
- Healthcare IoT for remote patient monitoring and telemedicine.
Common Pitfalls to Avoid
While RemoteIoT VPC is a powerful tool, there are some common pitfalls you should avoid:
- Not securing your devices properly, leaving them vulnerable to attacks.
- Overcomplicating your network setup, making it harder to manage.
- Ignoring performance optimization, leading to slow and inefficient systems.
Optimizing Performance
Once your RemoteIoT VPC is operational, optimizing its performance is crucial. Here are a few tips:
- Use load balancers to distribute traffic evenly across your devices.
- Implement caching to reduce latency and improve response times.
- Monitor your network performance regularly and make adjustments as needed.


Detail Author:
- Name : Mrs. Marilyne McKenzie
- Username : carolyn.schaefer
- Email : rosenbaum.amelia@yahoo.com
- Birthdate : 1993-03-24
- Address : 313 Goodwin Road Apt. 473 New Aleen, NY 25185-5789
- Phone : +1-351-658-1990
- Company : Hudson, Greenholt and Howell
- Job : Dredge Operator
- Bio : Iure sed iusto eligendi sit rerum. Rem unde saepe ducimus asperiores molestiae. Deserunt et unde et ullam nesciunt. Sit et et repellendus.
Socials
facebook:
- url : https://facebook.com/christian_cole
- username : christian_cole
- bio : Qui omnis aspernatur quia et sapiente quos non ab.
- followers : 4631
- following : 2352
instagram:
- url : https://instagram.com/colec
- username : colec
- bio : Eos consequuntur tempore sed aut dolor. Inventore excepturi sapiente voluptatem quam.
- followers : 4039
- following : 1835