IoT VPC Networks: Secure IoT In The Cloud Learn Now!
In an increasingly interconnected world, is your business equipped to handle the surge of data and potential vulnerabilities that come with the Internet of Things (IoT)? The answer lies, in part, with IoT VPC Networks, which provide a secure and scalable foundation for your IoT deployments.
The proliferation of IoT devices is reshaping industries, offering unprecedented opportunities for innovation and efficiency. From smart homes and connected cars to industrial automation and healthcare monitoring, the potential applications seem limitless. However, with this proliferation comes a critical need: the need for secure communication between these devices. IoT VPC Networks answer this call. These networks offer a dedicated, isolated environment within virtual private cloud (VPC) environments, allowing IoT devices to communicate and exchange data securely, without exposing sensitive information to the open internet. This article delves into the intricacies of IoT VPC Networks, exploring their benefits, outlining effective implementation strategies, and highlighting best practices to help you maximize their potential.
As we navigate the complex landscape of IoT VPC Networks, we'll consider how these networks align with modern security standards and compliance requirements. Ultimately, our goal is to provide a comprehensive understanding of why IoT VPC Networks are essential for businesses looking to leverage the transformative power of IoT while maintaining the highest levels of security.
Introduction to IoT VPC Networks
Benefits of IoT VPC Networks
Architecture of IoT VPC Networks
- Key Components of IoT VPC Networks
- How IoT VPC Networks Work
Security Considerations for IoT VPC Networks
Implementation Strategies
Scalability and Performance
Best Practices for IoT VPC Networks
- Network Segmentation
- Monitoring and Maintenance
Use Cases for IoT VPC Networks
Challenges and Solutions
Future Trends in IoT VPC Networks
Conclusion
Introduction to IoT VPC Networks
IoT VPC Networks represent a state-of-the-art approach to managing the complex demands of IoT devices within the secure confines of virtual private cloud environments. They create a dedicated and isolated space, where IoT devices can communicate with each other and seamlessly interact with cloud resources. This isolation is paramount because it protects the vital flow of data from external threats, ensuring that only authorized entities can access the sensitive information generated by IoT devices. By leveraging the power and flexibility of virtual private clouds, businesses can fortify their IoT ecosystems, shielding them from unauthorized access and the ever-present risk of cyberattacks.
The growth in the number of IoT devices is nothing short of exponential. As these devices become more prevalent, the need for robust, scalable connectivity solutions becomes more critical than ever. IoT VPC Networks directly address this need, offering a dedicated infrastructure that is meticulously designed to cater to the unique requirements of IoT devices. This includes support for low latency, the ability to handle high bandwidth demands, and the capability to process data in real-time. These features are critical for many IoT applications, ensuring efficiency and optimal performance.
According to a report by Gartner, the global IoT market is projected to surge to $1.1 trillion by 2027. The report highlights a compound annual growth rate (CAGR) of 24.5%. This remarkable growth rate underscores the undeniable importance of implementing robust and well-designed IoT VPC Networks. These networks are essential for supporting the expanding IoT landscape. They guarantee seamless integration with cloud-based systems, which, in turn, fosters innovation and fuels business growth.
Benefits of IoT VPC Networks
IoT VPC Networks provide businesses with a compelling array of advantages, making them an ideal choice for those seeking to implement secure and scalable IoT solutions. The benefits are far-reaching and include the following:
- Enhanced security through isolation and encryption
- Improved scalability to accommodate expanding IoT ecosystems
- Reduced latency and enhanced performance thanks to an optimized network architecture
- Centralized management and comprehensive monitoring of IoT devices
- Compliance with industry standards and regulations
By strategically leveraging these advantages, organizations can lay the groundwork for successful IoT initiatives. This, in turn, ensures long-term success and sustainability in an increasingly competitive digital landscape.
Architecture of IoT VPC Networks
Key Components of IoT VPC Networks
An IoT VPC Network consists of several crucial components that work in concert to ensure secure and efficient communication between IoT devices and cloud resources. These components are:
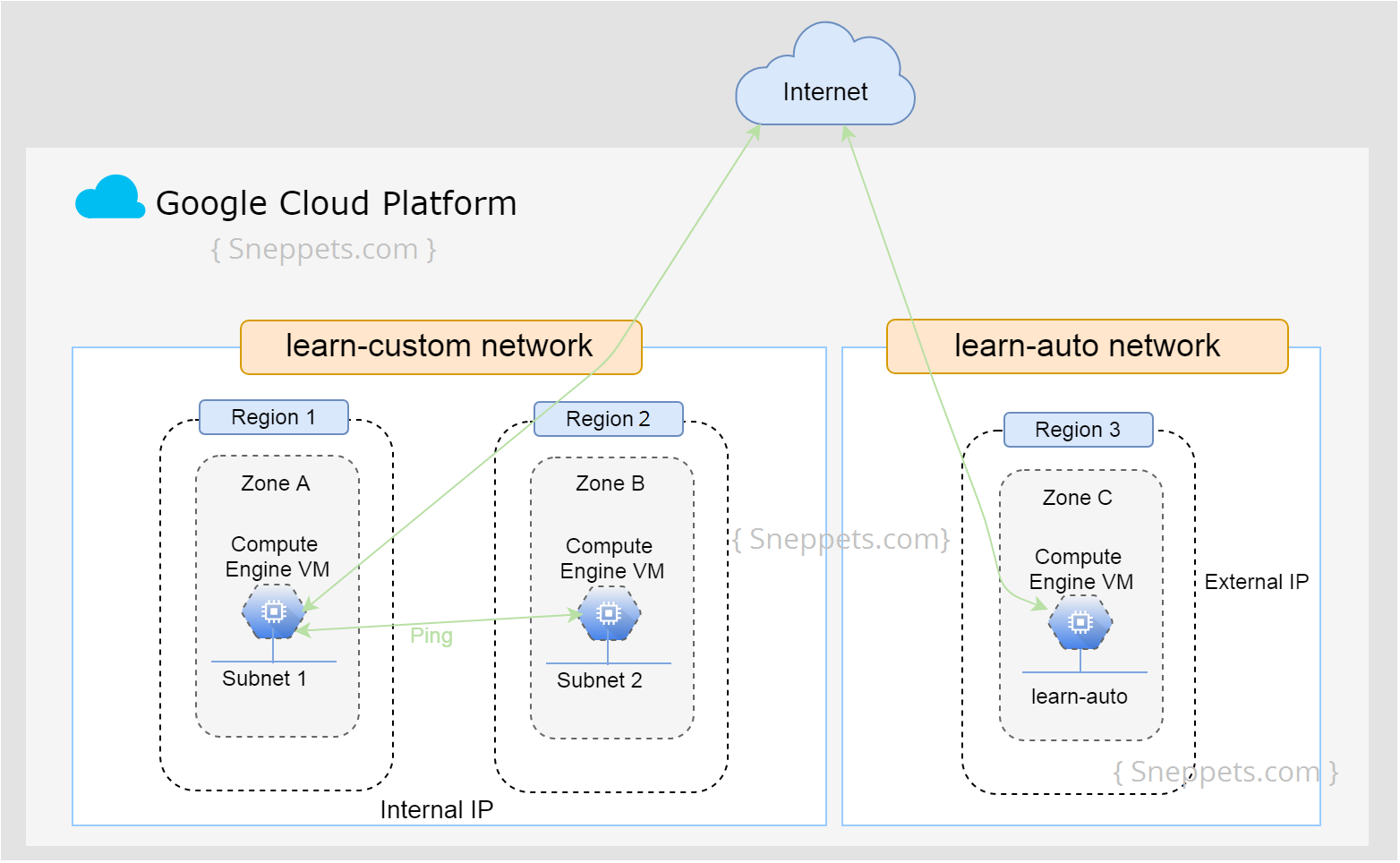
- Virtual Private Cloud (VPC): This is the private network environment that exists within the infrastructure of a public cloud provider.
- Subnets: These are logical divisions within the VPC that enable network segmentation and isolation, enhancing security and manageability.
- Security Groups: Functioning as firewalls, security groups control both inbound and outbound traffic for instances that reside within the VPC, acting as a critical layer of defense.
- Network Access Control Lists (NACLs): NACLs provide an additional layer of security, defining which traffic is allowed or denied at the subnet level.
- Gateways: Gateways create connections between the VPC and external networks, such as the internet or on-premises data centers.
How IoT VPC Networks Work
IoT VPC Networks operate by establishing a secure and isolated environment where IoT devices can communicate with each other and with the broader cloud resources. This is achieved through a combination of network segmentation, data encryption, and stringent access control mechanisms. This approach ensures that only authorized traffic is permitted within the VPC.
When an IoT device transmits data to the cloud, the data first passes through a gateway, which connects the VPC to the external network. The data is then routed through a series of subnets and security groups that have been configured to enforce strict access control policies. This crucial step guarantees that only trusted devices and applications are able to access the data. This meticulous process is pivotal in safeguarding sensitive information and preventing unauthorized access to the IoT ecosystem, safeguarding the data's integrity and confidentiality.
Security Considerations for IoT VPC Networks
While IoT VPC Networks offer a significant upgrade in security compared to traditional networking approaches, there are several key factors that organizations must carefully consider when implementing these systems. These include:
- Ensuring proper configuration of security groups and NACLs to prevent any unauthorized access to the network.
- Implementing strong encryption protocols to ensure the safety of data, both during transit and while at rest.
- Regularly updating and patching IoT devices and cloud resources to eliminate any potential vulnerabilities and maintain a secure environment.
- Continuously monitoring network activity for any unusual patterns of behavior or suspicious activity that could pose a threat to the network.
By taking these considerations into account and proactively addressing them, organizations can significantly strengthen the security of their IoT VPC Networks. This proactive approach protects their valuable assets from the ever-present threat of cyberattacks, ensuring business continuity and safeguarding sensitive data.
Implementation Strategies
The successful deployment of an IoT VPC Network is a process that demands careful planning and meticulous execution. To achieve optimal results, several key strategies should be followed:
- Defining clear objectives and specific requirements for the IoT VPC Network. This step provides a roadmap for the entire implementation process.
- Selecting the most appropriate cloud provider and carefully choosing the specific services that will best support the network's operation.
- Designing a network architecture that is not only scalable but also flexible enough to accommodate future growth and evolving needs.
- Establishing strong and comprehensive security policies and procedures that will effectively protect the network from potential threats.
By adhering to these strategies, organizations can confidently ensure their IoT VPC Networks are implemented efficiently. They can also be confident that they will deliver the desired results, supporting business objectives and paving the way for future innovation.
Scalability and Performance
IoT VPC Networks are specifically designed to meet the demanding scalability and performance requirements that are inherent in modern IoT ecosystems. They leverage the powerful capabilities of virtual private clouds, allowing them to dynamically scale to accommodate the ever-increasing numbers of devices and the substantial data volumes they generate. This dynamic scaling ensures that the network remains responsive, even during periods of peak demand.
The network's design is also optimized for performance. Advanced routing algorithms contribute to minimizing latency and enhancing overall performance, ensuring the smooth and efficient flow of data. This, in turn, allows for quicker response times and improved user experiences.
According to a study by Cisco, global IoT traffic is projected to hit an astounding 1.5 zettabytes annually by 2023. This figure underscores the essential role of scalable, high-performance IoT VPC Networks. These networks are crucial for managing this extraordinary growth and ensuring that the digital landscape remains robust and efficient.
Best Practices for IoT VPC Networks
Network Segmentation
Network segmentation is a crucial practice for IoT VPC Networks. It isolates different parts of the network and significantly reduces the overall attack surface. By dividing the network into smaller, distinct subnets, organizations can effectively limit the potential impact of any security breach. This targeted approach guarantees that sensitive data remains protected. It prevents the scope of any potential compromise from extending throughout the entire network infrastructure.
Monitoring and Maintenance
Regular monitoring and ongoing maintenance are essential for ensuring the continuous security and optimal performance of IoT VPC Networks. This means constantly watching network activity for any anomalies or unusual patterns that could indicate a potential issue. It also requires performing routine updates and promptly applying security patches. Proactive maintenance involves addressing any issues that arise promptly and efficiently.
| IoT VPC Networks | Details |
|---|---|
| Definition | A network built within a virtual private cloud (VPC) designed to provide secure and scalable connectivity for Internet of Things (IoT) devices. It isolates IoT devices and their communications, enhancing security and performance. |
| Key Components | Includes VPC, Subnets, Security Groups, Network Access Control Lists (NACLs), and Gateways. These elements work together to create a secure and controlled network environment. |
| Benefits | Offers enhanced security (isolation, encryption), improved scalability, reduced latency, centralized management, and compliance with industry standards and regulations. |
| Use Cases |
|
| Security Considerations | Requires proper configuration of security groups and NACLs, strong encryption protocols, regular updates and patching of devices and resources, and continuous monitoring for suspicious activity. |
| Implementation Strategies | Involves defining clear objectives, selecting the right cloud provider and services, designing a scalable architecture, and establishing robust security policies. |
| Scalability and Performance | Designed to scale with increasing numbers of devices and data volumes, using optimized network architectures and routing algorithms to minimize latency and improve performance. |
| Best Practices | Include network segmentation (isolating parts of the network) and regular monitoring and maintenance (updates, patching, addressing issues). |
| Challenges | Can involve complexity in design and implementation, associated costs, and ensuring compatibility with existing systems. |
| Future Trends | Likely to see increased adoption of edge computing, advancements in AI and machine learning for network management, and a greater emphasis on cybersecurity. |
| Reference | Example Guide on IoT VPC Networks (Replace with a real, credible source link) |

Detail Author:
- Name : Henderson Schoen
- Username : prosacco.naomie
- Email : lupe.predovic@kihn.com
- Birthdate : 1980-02-22
- Address : 355 Nicolas Forest Kozeyland, WA 64497-6653
- Phone : 1-651-840-0593
- Company : Conn-Treutel
- Job : Nuclear Equipment Operation Technician
- Bio : Doloribus culpa saepe facilis nesciunt vel quia. Sed itaque sapiente ratione eum assumenda ut sit. Sequi id dolores et unde sit.
Socials
facebook:
- url : https://facebook.com/arlo_official
- username : arlo_official
- bio : Iure ut modi harum. Fugit cumque dolore eligendi.
- followers : 6573
- following : 1389
linkedin:
- url : https://linkedin.com/in/arlo.jerde
- username : arlo.jerde
- bio : Sunt neque optio natus dolore voluptates.
- followers : 434
- following : 323
instagram:
- url : https://instagram.com/arlojerde
- username : arlojerde
- bio : Rem sit nihil sunt sunt in a iste. Id reiciendis repellendus ut.
- followers : 3596
- following : 2344
twitter:
- url : https://twitter.com/arlojerde
- username : arlojerde
- bio : Possimus laudantium et quam ut quae. Et ut excepturi dolores numquam. Tempora quia doloremque expedita qui eveniet.
- followers : 6318
- following : 2146