RemoteIoT VPC SSH Raspberry Pi Download: Your Ultimate Guide
Is it truly possible to manage an entire network of Internet of Things (IoT) devices from the comfort of your own home, or even across the globe? The answer, increasingly, is a resounding yes. This is made possible by leveraging technologies like Virtual Private Clouds (VPCs), Secure Shell (SSH) connections, and the ever-versatile Raspberry Pi a combination that's revolutionizing the way we interact with and control our connected devices.
IoT technology is transforming various sectors, from smart homes and industrial automation to environmental monitoring and healthcare. Central to this transformation is the ability of devices to communicate and share data seamlessly. However, the inherent challenges of managing these devices remotely including network complexities, cloud computing intricacies, and robust cybersecurity considerations can seem daunting. This exploration delves into the practicalities of RemoteIoT VPC SSH Raspberry Pi setups, providing a comprehensive understanding of the tools, processes, and best practices necessary to navigate this evolving landscape.
Before diving into the technical aspects, let's clarify the core concepts. RemoteIoT essentially refers to the capability to remotely manage, monitor, and interact with IoT devices. This offers unparalleled flexibility and scalability. Businesses and individuals alike can leverage cloud computing and secure communication protocols to control devices without the need for physical presence. A critical element in this architecture is the use of a Virtual Private Cloud (VPC).
- Discover Sone 260 Your Digital Transformation Starts Now
- Is Job Mccully Alive Debunking The Rumors Amp Career
A VPC acts as a dedicated and isolated network environment within a cloud platform, such as Amazon Web Services (AWS) or Microsoft Azure. Think of it as your private, secure network within the larger internet cloud. This isolation is essential for the security and performance of your applications and services, especially when dealing with sensitive data or critical operations. When combined with RemoteIoT, a VPC provides a solid framework for managing IoT devices. The benefits are numerous, including:
- Enhanced efficiency in device management.
- Reduced operational costs by minimizing on-site visits.
- Fortified security through encrypted connections.
- Scalability to easily accommodate expanding IoT networks.
The Raspberry Pi, a compact and cost-effective single-board computer, is a cornerstone of many RemoteIoT setups. Its versatility and user-friendliness make it an ideal choice for implementing IoT solutions. The Raspberry Pi's popularity stems from its ability to support a variety of operating systems and programming languages, allowing for customization to meet specific project needs. Some key advantages include:
- Cost-effective hardware solution.
- Extensive community support and resources.
- Compatibility with numerous sensors and peripherals.
- Low power consumption for long-term deployments, making it suitable for remote applications.
Now, let's consider the heart of secure remote access: Secure Shell (SSH). SSH is a cryptographic network protocol that ensures data transmitted between devices and the cloud is encrypted and protected from unauthorized access. Understanding SSH basics is crucial for any secure IoT environment. It is responsible for creating an encrypted connection between a client and a server. This involves several key steps:
- Full Hd Sexy Movies Everything You Need To Know Trends Production More
- Temporary Replacement 3 Your Guide To Business Continuity
- Authentication using passwords or public key cryptography.
- Data encryption to prevent eavesdropping.
- Integrity checks to ensure data hasn't been tampered with.
The combination of VPC, SSH, and Raspberry Pi opens up a world of possibilities for controlling and monitoring devices remotely. To provide a clearer picture, imagine the following scenario: A company, "EcoTech Solutions," specializes in environmental monitoring. They deploy a network of Raspberry Pi-based sensors in various locations, collecting data on air quality, temperature, and humidity. Through a VPC, EcoTech can securely access these sensors remotely, monitor their performance, update their software, and retrieve collected data without ever setting foot on-site. This translates to significant cost savings, increased efficiency, and enhanced data security.
The setup process, though it might seem complex at first, can be broken down into manageable steps. Let's delve into the key aspects:
Setting Up RemoteIoT VPC
Setting up a VPC for RemoteIoT involves several key steps:
- Create a VPC: This is the foundation of your private network. Use your chosen cloud provider's console (AWS, Azure, Google Cloud, etc.) to create a new VPC. You'll need to specify the IP address range for your VPC (e.g., 10.0.0.0/16) and other settings, such as the VPC name and tenancy.
- Define Subnets: Subnets divide your VPC into smaller, more manageable network segments. It's recommended to create both private and public subnets. Private subnets are designed for devices that don't need direct internet access (like your Raspberry Pis), while public subnets have a route to the internet via an internet gateway. Ensure you create the subnets in the different availability zones (AZ) your cloud provider supports to make your services more reliable.
- Configure Security Groups: Security groups act as virtual firewalls, controlling inbound and outbound traffic for your instances (e.g., your Raspberry Pi instances). You define rules to allow or deny traffic based on protocols (e.g., SSH on port 22), ports, and source IP addresses. In your security group for the Raspberry Pi instances, you would typically allow SSH traffic (port 22) from your trusted IP addresses.
- Configure Network Access Control Lists (NACLs) NACLs provide another layer of security. While security groups act at the instance level, NACLs control traffic at the subnet level. NACLs are stateless, so you'll need to define both inbound and outbound rules. You can use NACLs to block all traffic to the subnet except from a very specific and limited list of IP addresses, protecting your IoT devices.
- Deploy Instances: Once the VPC and subnet are configured, you can deploy your Raspberry Pi instances within the private subnet. You will need to provision a method to allow the raspberry pi to initiate a connection to the cloud, like installing an SSH agent for reverse SSH connections, or other VPN solutions.
Configuring SSH on Raspberry Pi
Configuring SSH on a Raspberry Pi is essential for secure remote access. Here's a guide:
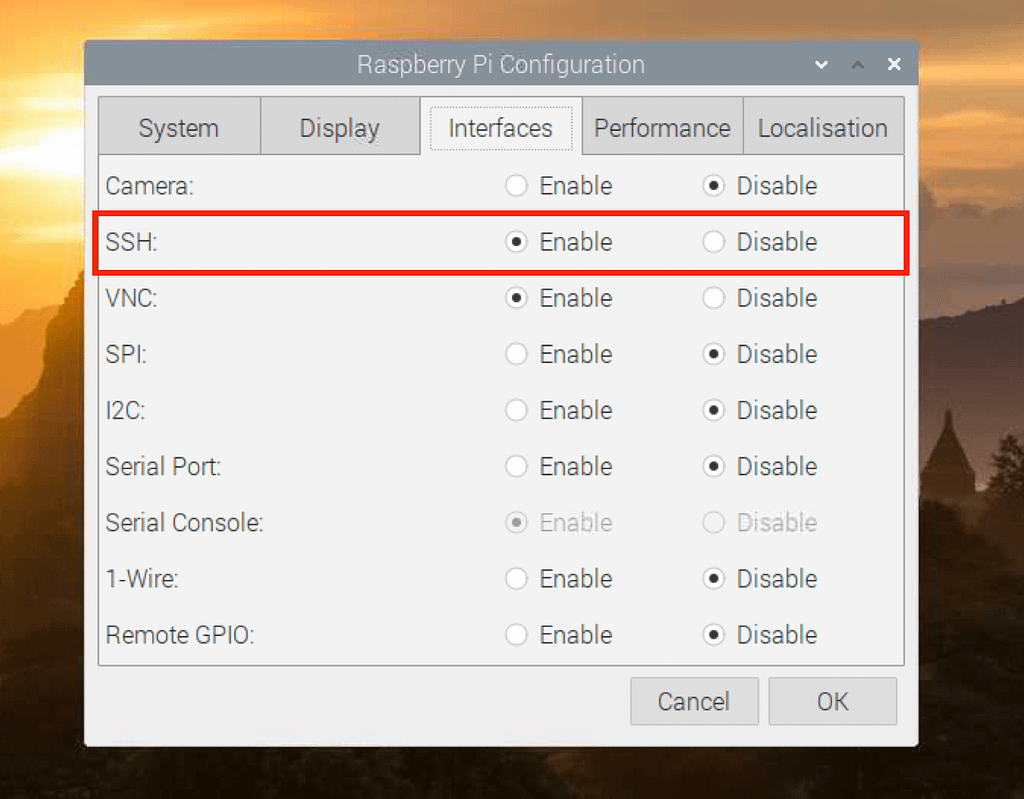
- Enabling SSH: You can enable SSH through the Raspberry Pi Configuration tool or by creating an empty file named "ssh" (without the quotes and with no file extension) on the boot partition of your Raspberry Pi's SD card.
- Securing SSH: Once enabled, enhance security:
- Change the default SSH port (22) to a non-standard value to deter automated attacks.
- Disable password authentication. Instead, use public key authentication. This involves generating an SSH key pair on your local machine and copying the public key to the Raspberry Pi's authorized_keys file.
- Limit SSH access to specific IP addresses. Use firewall rules (e.g., `iptables` or `ufw`) to allow SSH traffic only from your trusted IP addresses or a range of addresses.
Downloading RemoteIoT VPC Components
Downloading the necessary components for your RemoteIoT VPC setup is another critical step:
- Identify Required Components: Determine which software and libraries are needed. Common components include:
- SSH server software (e.g., OpenSSH on the Raspberry Pi).
- Cloud provider SDKs (e.g., AWS SDK for Python, or Azure SDK for Python) if you want to manage your VPC through code.
- IoT device drivers and libraries for interacting with your sensors or peripherals.
- Access Repositories: Download the required components from official repositories or trusted third-party sources. Always verify the integrity of the downloaded files (e.g., using checksums) to ensure you're getting authentic and untampered software.
Security Best Practices
Security is paramount when dealing with RemoteIoT setups. To ensure your devices and data are protected, adhere to these best practices:
- Regular Updates: Regularly update your operating system, applications, and firmware to patch vulnerabilities. Automated update mechanisms are very helpful.
- Network Segmentation: Use VPCs and subnets to isolate IoT devices from other network resources.
- Monitoring and Logging: Implement robust monitoring tools (e.g., Nagios, Zabbix) to detect suspicious activities. Enable logging and regularly review logs for any anomalies.
- Strong Passwords/Key Management: Enforce strong passwords, and, even better, disable password authentication and rely on SSH keys with passphrases. Regularly rotate keys.
- Least Privilege: Grant only the necessary permissions to users and devices.
- Two-Factor Authentication (2FA): Where possible, enable 2FA on your cloud accounts and SSH access.
- Regular Audits: Conduct regular security audits and penetration tests to identify vulnerabilities.
Troubleshooting Tips
Encountering issues is a common part of any technical setup. Here are some troubleshooting tips:
- Check Network Configuration: Ensure that your network settings are correct, including IP addresses, subnets, and security group rules. Use tools like `ping`, `traceroute`, and `netstat` to diagnose network connectivity.
- Verify SSH Settings: Double-check your SSH configuration files (e.g., `/etc/ssh/sshd_config` on the Raspberry Pi) for errors or misconfigurations. Pay close attention to port numbers, authentication methods, and access control settings.
- Consult Documentation: Refer to official documentation and online forums for guidance. Resources from your cloud provider (AWS, Azure, etc.) and the Raspberry Pi community can be invaluable.
- Firewall Configuration: Make sure that the firewall on your Raspberry Pi (e.g., using `ufw` or `iptables`) is not blocking SSH traffic.
- Connectivity Issues: Verify that the Raspberry Pi has network connectivity and can reach the internet. Use `ping` to test this.
Now, let's get into some advanced features and considerations.
Reverse SSH Tunnels for Dynamic IPs: One common challenge is dealing with Raspberry Pis that have dynamic IP addresses. Since the IP address changes frequently, connecting to it directly becomes difficult. A solution is to use reverse SSH tunnels. This involves the Raspberry Pi initiating an SSH connection outward to a server with a known, static IP address. You can then connect to the Raspberry Pi by connecting to the server and accessing the tunnel.
SSH Key Management: The most secure way to access your Raspberry Pi is to use SSH keys. Instead of using a password, you generate a key pair (a public key and a private key). You then copy the public key to the Raspberry Pi. When you try to connect, you use the private key, and SSH automatically uses this to authenticate. This is a much more secure approach than password-based authentication.
Automated Configuration: To streamline the setup process, consider using configuration management tools. These tools help automate the configuration of your Raspberry Pis. Examples include Ansible, Puppet, and Chef. These tools let you define the desired state of your Raspberry Pi configuration, and the tool will take care of applying those changes. This is a huge time saver, especially if you have multiple devices.
Choosing a Cloud Provider: The choice of cloud provider will influence the specifics of your VPC setup. The major players are Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). Each offers a wide range of services. Choosing the right provider will depend on your budget, specific requirements, and expertise.
Monitoring Your IoT Devices: Monitoring is a crucial aspect of IoT management. Tools like Prometheus and Grafana are often used to collect and visualize data from your Raspberry Pis and other devices. These tools help you track the performance, health, and status of your devices. This helps you identify issues quickly and respond proactively.
Edge Computing: Edge computing moves processing closer to the data source (your Raspberry Pis). This can improve latency, reduce bandwidth usage, and enhance security. Instead of sending all the data to the cloud, you can perform some processing locally on the Raspberry Pi itself. For example, you could perform initial data filtering or analysis.
Containerization: Using containers (like Docker) can help package your applications and their dependencies. Containers provide a consistent environment that makes it easier to deploy and manage your IoT applications. You can use Docker Compose to define and manage multi-container applications.
Security Considerations: Security must be top-of-mind. Here's a deeper look:
- Regular Security Audits: Conduct regular security audits. This helps identify vulnerabilities and ensure that your system is secure.
- Vulnerability Scanning: Use vulnerability scanning tools to scan your Raspberry Pis and the other components of your system.
- Intrusion Detection Systems (IDS): Consider using an IDS to detect malicious activity.
- Secure Boot: If possible, enable secure boot on your Raspberry Pis.
- Over-the-Air (OTA) Updates: Implement a secure OTA update mechanism. This allows you to update the software on your Raspberry Pis remotely. Make sure that the updates are signed.
The following table is related to the key components and configuration of remote IoT using VPC, SSH, and Raspberry Pi.
| Component | Description | Configuration Steps |
|---|---|---|
| Virtual Private Cloud (VPC) | A logically isolated network within a cloud platform. Provides a secure environment for your IoT devices. |
|
| Secure Shell (SSH) | A cryptographic protocol used to secure network communications, ensuring encrypted and protected data transfer. |
|
| Raspberry Pi | A compact, affordable single-board computer ideal for IoT projects. |
|
| IoT Devices & Sensors | Connected devices that collect and transmit data. |
|
| Cloud Provider Services | Services provided by cloud platforms for managing and securing the infrastructure. |
|
As with any technological undertaking, this process is filled with complexities that necessitate careful planning and execution. The successful implementation of a RemoteIoT VPC SSH Raspberry Pi setup relies on a solid understanding of networking fundamentals, cloud computing best practices, and robust security measures. By following the steps outlined here and embracing the insights provided, you're on your way to building a reliable and efficient remote IoT environment tailored to meet the unique demands of your project. Remember that this is an ongoing journey of learning and adaptation. Continuous innovation and exploration within this dynamic field will keep you at the forefront of technological advancements.

Detail Author:
- Name : Mrs. Shanon Feeney
- Username : carol.jacobi
- Email : vzulauf@wolff.com
- Birthdate : 1992-05-31
- Address : 6236 Carroll Crest Zoieside, LA 11361
- Phone : (303) 232-3720
- Company : Windler Group
- Job : Plating Operator OR Coating Machine Operator
- Bio : Ipsum commodi id vel doloribus sunt ipsam quia. Praesentium corporis dolores odio dignissimos temporibus amet. Magni quia deserunt praesentium aut qui omnis eius. Voluptatem vitae sunt consequatur.
Socials
tiktok:
- url : https://tiktok.com/@hollis3502
- username : hollis3502
- bio : In officiis nesciunt reprehenderit ducimus sunt error quo.
- followers : 2171
- following : 711
linkedin:
- url : https://linkedin.com/in/hollistreutel
- username : hollistreutel
- bio : Rem dolorum qui minima dolorem.
- followers : 3298
- following : 1746