Secure IoT: Raspberry Pi & VPC Setup Guide | [Your Website Name]
In an increasingly interconnected world, is it possible to safeguard your Internet of Things (IoT) devices from cyber threats? Absolutely. Setting up a Virtual Private Cloud (VPC) using a Raspberry Pi offers a robust and secure solution, essential for both developers and technology enthusiasts. With the proliferation of smart devices and the data they generate, the need for secure communication and data transfer has never been greater. This guide provides a comprehensive walkthrough of how to establish a secure connection for your IoT devices using a Raspberry Pi, while also highlighting readily available free resources to enhance your projects.
Whether you're a seasoned developer or just beginning your journey into the world of IoT, this resource provides step-by-step instructions and valuable insights into securing your devices. By the end of this article, you'll possess a thorough understanding of how to build a secure environment for your IoT projects, minimizing risk and maximizing performance.
This article delves into practical solutions, real-world examples, and expert advice, ensuring your IoT setup is both secure and efficient. Let's explore the specifics and discover how to achieve a secure connection for your remote IoT devices utilizing a Raspberry Pi.
- Im Sorry Alternatives To Full Open Sexy Videos Great Content Ideas
- Masafun Your Travel Hub Find Adventures Amp Connect
Table of Contents
- Introduction to IoT VPC
- Raspberry Pi Setup
- Secure Communication Protocols
- VPC Configuration for IoT
- Remote Access Solutions
- Free Resources for IoT Projects
- Troubleshooting Common Issues
- Best Practices for IoT Security
- Case Studies and Real-World Examples
Introduction to IoT VPC
A Virtual Private Cloud (VPC) is a foundational element in protecting your IoT devices. It creates an isolated and secure environment where your devices can communicate without exposing sensitive data to the public internet. By utilizing a VPC, you maintain control over device access and ensure only authorized users can interact with them. This is a critical step in ensuring the integrity and confidentiality of your data.
Why Use VPC for IoT?
- 9inch Pizza Craze Why This Size Is Your Next Favorite Bite
- Hilton Garden Inn Atlanta Midtown Your Guide To A Great Stay
Employing a VPC for your IoT infrastructure offers several advantages:
- Enhanced security by isolating devices from the open internet, reducing the attack surface.
- Improved performance through reduced latency and optimized data transfer, which is crucial for real-time applications.
- Granular control over network traffic and access permissions, allowing you to tailor security policies to your specific needs.
VPCs are particularly valuable for remote IoT devices that frequently exchange data. They help maintain a secure and reliable connection, ensuring smooth operation even in challenging environments where network stability might be inconsistent.
Raspberry Pi Setup
The Raspberry Pi is a versatile and affordable single-board computer, an ideal platform for managing and securing your IoT devices. Setting up a Raspberry Pi for your IoT projects involves several steps, from hardware configuration to software installation, each playing a crucial role in the overall security and functionality.
Steps to Set Up Raspberry Pi
Here is a guide for setting up your Raspberry Pi:
- Install the latest version of Raspberry Pi OS (formerly Raspbian) onto your SD card. This operating system is optimized for the Raspberry Pi and provides a stable base for your IoT projects.
- Connect your Raspberry Pi to a monitor, keyboard, and mouse. This allows for initial configuration and troubleshooting.
- Update the operating system using the command
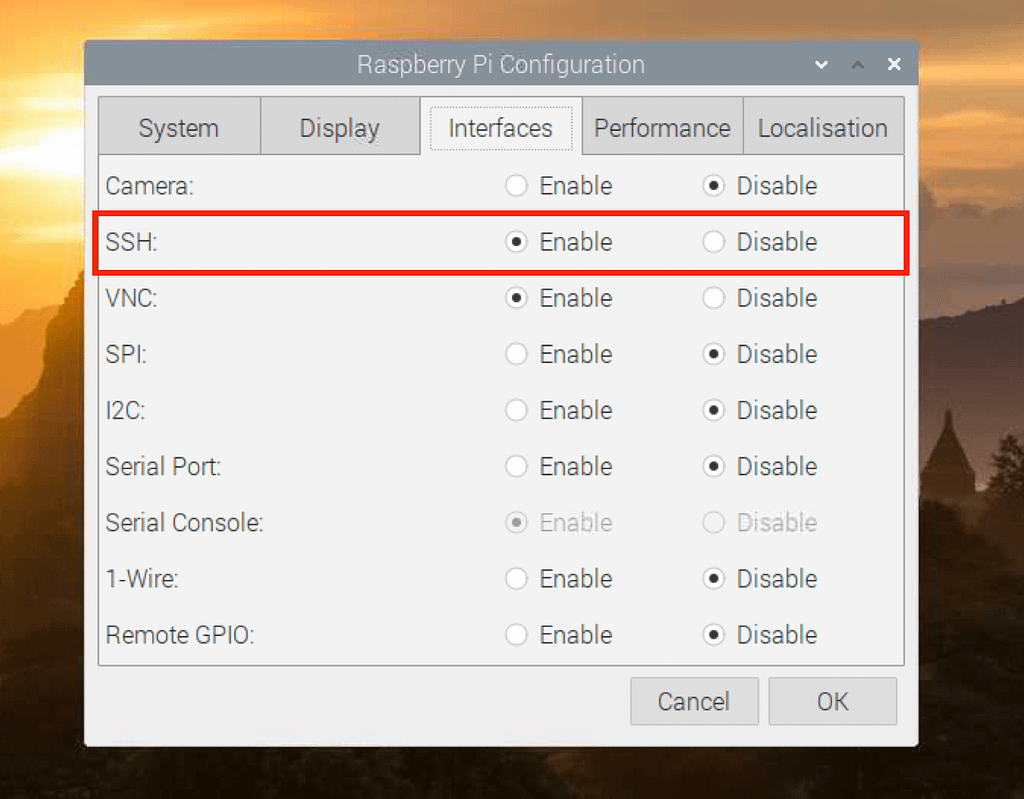
sudo apt update && sudo apt upgrade. This process ensures that your system has the latest security patches and software updates. - Install necessary software packages, such as SSH (Secure Shell) and VNC (Virtual Network Computing), for remote access. These tools enable you to manage your Raspberry Pi from a remote location, critical for IoT deployments.
With your Raspberry Pi configured, you can proceed to configure it for your IoT applications. This involves setting up network connections, installing necessary software for data collection and transmission, and finally, integrating it into your VPC, ensuring it's ready to connect securely.
Secure Communication Protocols
Securing communication between your IoT devices and your VPC is paramount for safeguarding sensitive data. Several protocols are available to achieve this, each with its own advantages and disadvantages. The choice of protocol depends on your specific requirements.
Choosing the Right Protocol
Each protocol has its specific strengths and weaknesses:
- MQTT: MQTT (Message Queuing Telemetry Transport) is a lightweight protocol ideal for low-bandwidth environments, making it suitable for devices with limited resources.
- HTTPS: HTTPS (Hypertext Transfer Protocol Secure) is widely used for secure web communications.
- TLS: TLS (Transport Layer Security) provides end-to-end encryption for secure data transfer, protecting data in transit.
Selecting the appropriate protocol depends on your specific use case and the requirements of your IoT project, considering factors like bandwidth, security needs, and the capabilities of your devices.
VPC Configuration for IoT
Configuring a VPC for IoT involves setting up subnets, security groups, and access control lists to ensure secure communication between your devices. This is a critical step in creating a private, isolated network.
Key Steps in VPC Configuration
Here are the essential steps to configure your VPC:
- Create a VPC with a unique CIDR (Classless Inter-Domain Routing) block. The CIDR block defines the range of IP addresses your VPC will use.
- Set up public and private subnets to segregate device traffic. Public subnets can be used for devices needing internet access, while private subnets are ideal for more secure, internal communication.
- Configure security groups to define access rules for your devices. These act as virtual firewalls, controlling inbound and outbound traffic.
- Utilize NAT (Network Address Translation) gateways to allow private devices to access the internet securely. This provides a secure way for your devices to reach external resources while keeping their internal IP addresses private.
By following these steps, you can establish a robust VPC environment specifically designed to meet the demands of your IoT needs, offering both security and flexibility.
Remote Access Solutions
Remote access is crucial for managing IoT devices deployed in remote locations. Several tools and methods facilitate secure remote access, including SSH, VPN, and cloud-based solutions. Choose the one that best suits your operational needs.
Best Tools for Remote Access
Consider the following tools for secure remote access:
- SSH: SSH (Secure Shell) provides a secure protocol for accessing remote devices via the command line, offering a robust method for system administration.
- VPN: A VPN (Virtual Private Network) offers encrypted access to your VPC from any location, enhancing security for remote users.
- Cloud Services: Platforms such as AWS IoT Core offer built-in remote access capabilities, simplifying management and integration.
Each tool offers unique advantages, so selecting the one that best aligns with your project's requirements is essential for successful deployment and management.
Free Resources for IoT Projects
Numerous free resources are available to enhance your IoT projects. These resources can significantly reduce development costs while providing valuable insights.
Top Free Resources for IoT
Here are some of the best free resources for IoT:
- Raspberry Pi Documentation: Comprehensive guides and tutorials for setting up and using Raspberry Pi.
- MQTT Eclipse: Open-source MQTT broker and client tools.
- GitHub Repositories: A vast collection of IoT projects and code samples.
By leveraging these resources, you can accelerate your IoT development and achieve better results.
Troubleshooting Common Issues
Despite careful planning, challenges can arise when setting up and managing IoT devices. Understanding common problems and their solutions is vital for effective troubleshooting. Being prepared can save significant time and effort.
Common Issues and Solutions
Here are some common issues and their solutions:
- Connection Failures: Check network settings and ensure all devices are correctly configured. Verify IP addresses, subnet masks, and gateway settings.
- Security Breaches: Regularly update software and utilize robust encryption protocols. Implement firewalls, intrusion detection systems, and regular security audits.
- Performance Issues: Optimize data transfer and minimize unnecessary traffic. Compress data, use efficient protocols, and monitor network performance.
By addressing these issues promptly, you can maintain a stable and secure IoT environment. Regular monitoring and maintenance are essential.
Best Practices for IoT Security
Implementing best practices is essential for ensuring the security of your IoT devices. These practices encompass everything from device configuration to network management and are vital for protecting your infrastructure.
Key Best Practices
Here are some best practices to follow:
- Regularly update firmware and software to protect against vulnerabilities. Enable automatic updates and stay informed about security advisories.
- Use strong passwords and multi-factor authentication for device access. This greatly reduces the risk of unauthorized access.
- Monitor network traffic for suspicious activity and respond quickly to potential threats. Implement intrusion detection systems and log all network activity.
Adhering to these practices helps maintain a secure and reliable IoT infrastructure, minimizing the risk of breaches and data loss.
Case Studies and Real-World Examples
Examining real-world examples provides valuable insights into how to successfully implement secure IoT solutions. These case studies highlight the challenges and solutions encountered across diverse industries.
Case Study: Smart Agriculture
In the agriculture industry, IoT devices monitor soil moisture, temperature, and other environmental factors. By connecting these devices securely to a VPC using a Raspberry Pi, farmers can make data-driven decisions to optimize crop yields. This allows for efficient resource management and increased productivity.
Case Study: Smart City Surveillance
In several urban centers, IoT devices like security cameras and environmental sensors are deployed to monitor public safety and environmental conditions. A secure VPC, managed by Raspberry Pis, ensures the private network for data transmission, helping prevent cyber threats and ensure privacy for citizens. Using Raspberry Pis as the gateway allows for efficient processing of data at the edge, enhancing data security, and minimizing latency.
Case Study: Industrial Automation
Manufacturers employ IoT to monitor machinery and processes, using real-time data to optimize production. Securing these devices within a VPC, managed by a Raspberry Pi, safeguards critical operational data, and prevents disruption. The Raspberry Pi's compact design and low power consumption make it perfectly suited for factory environments, allowing secure data flow and ensuring system reliability.

Detail Author:
- Name : Mallory Boyle
- Username : owiegand
- Email : ervin.labadie@boyer.com
- Birthdate : 2002-12-25
- Address : 8549 Otha Mall Lake Daphney, LA 62644
- Phone : 1-469-912-1135
- Company : Fahey Inc
- Job : Data Processing Equipment Repairer
- Bio : Consequatur cupiditate in quod amet voluptatem aut. Id porro beatae cupiditate. Esse velit excepturi magnam officiis ipsum vel excepturi.
Socials
facebook:
- url : https://facebook.com/ophelia.kshlerin
- username : ophelia.kshlerin
- bio : Consequatur voluptatem quod omnis nulla qui voluptatem aut eum.
- followers : 3729
- following : 104
instagram:
- url : https://instagram.com/ophelia_xx
- username : ophelia_xx
- bio : Magnam mollitia ipsam neque accusamus ad. Velit ducimus quo ut ut voluptas nisi.
- followers : 6310
- following : 818
linkedin:
- url : https://linkedin.com/in/okshlerin
- username : okshlerin
- bio : Tempore qui iusto debitis exercitationem.
- followers : 5181
- following : 615