Secure IoT & VPC: Raspberry Pi Setup & Free Downloads Guide
In an era where connectivity reigns supreme, can you afford to overlook the security of your Internet of Things (IoT) devices? Securely connecting remote IoT devices to a Virtual Private Cloud (VPC) using a Raspberry Pi is not just a technical exercise; it's a fundamental requirement for maintaining data integrity and operational resilience.
The proliferation of smart devices, from household appliances to industrial sensors, has created a vast and often vulnerable attack surface. Securing these devices and the data they generate demands a proactive and multifaceted approach. This article provides a roadmap for establishing secure communication channels for your IoT devices, focusing on the practical application of Raspberry Pi within a VPC environment. We will delve into the core concepts, explore actionable strategies, and identify free resources to strengthen your IoT infrastructure. Our aim is to equip you with the knowledge and tools necessary to protect your devices and data against the growing threat landscape.
This is the place where your detailed information and table should be placed.
- Car Insurance In Camp Hill Your Guide To Protection Savings
- Professional Dupes Save Money Get The Look You Love
IoT security is not merely a technical challenge; it's a critical imperative in today's connected world. As IoT devices become increasingly integrated into critical systems, the potential consequences of a security breach escalate dramatically. A compromised device can serve as a gateway to sensitive data, enabling attackers to steal information, disrupt operations, or even cause physical harm. Protecting these devices, which range from smart thermostats to sophisticated industrial sensors, demands a proactive and layered approach. By prioritizing robust security measures, organizations can mitigate the risks associated with IoT deployments and ensure the integrity and availability of their systems.
What is IoT Security?
IoT security encompasses the technologies and practices employed to safeguard IoT devices and the networks to which they connect. These devices, often characterized by their limited computing power and inherent vulnerabilities, represent attractive targets for cybercriminals. Securing remote IoT devices ensures that sensitive information is protected, unauthorized access is prevented, and the operational integrity of the devices and their associated systems is maintained.
Why is IoT Security Crucial?
The integration of IoT devices into critical infrastructure, such as healthcare, manufacturing, and transportation, has amplified the importance of robust security measures. A breach in a single device can have far-reaching consequences, including data theft, financial losses, and physical damage. Securing remote IoT VPC connections enables organizations to:
- Masafun Your Travel Hub Find Adventures Amp Connect
- Sydney Sweeney In Handmaids Tale Casting Rumors Explored
- Protect confidential information from unauthorized access.
- Prevent malicious actors from gaining control of devices.
- Ensure compliance with relevant industry regulations and standards.
Common IoT Security Threats
A thorough understanding of potential threats is the first line of defense in securing your IoT environment. Some of the most prevalent threats include:
- Device hijacking: Attackers gain control of IoT devices to perform malicious activities, such as launching denial-of-service attacks or stealing sensitive data.
- Data breaches: Unauthorized access to sensitive data transmitted between devices or stored on the devices themselves.
- Firmware vulnerabilities: Exploiting weaknesses in outdated or unpatched firmware to compromise devices and gain access to the network.
This is the place where your detailed information and table should be placed.
A Virtual Private Cloud (VPC) provides a secure and isolated network environment within the cloud, offering enhanced security and control over your IoT devices. A VPC acts as a private network, enabling you to host and manage your devices in a controlled setting, effectively shielding them from external threats and ensuring secure communication. This isolation is crucial for maintaining the confidentiality, integrity, and availability of your IoT infrastructure. By leveraging a VPC, you can establish a robust and scalable foundation for your IoT deployments, allowing your devices to function securely and reliably.
What is a VPC?
A Virtual Private Cloud (VPC) is a secure and isolated network environment provided by cloud service providers, such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP). It allows you to create a private network within the cloud infrastructure, providing greater control over your network configuration and security settings.
Benefits of Using a VPC for IoT
Implementing a VPC for your IoT devices offers several advantages:
- Enhanced security through network isolation: VPCs isolate your IoT devices from the public internet and other potentially vulnerable systems.
- Flexible configuration options for device management: You can customize your VPC to meet the specific needs of your IoT deployments, including IP addressing, subnets, and routing.
- Scalability to accommodate growing IoT deployments: VPCs can easily scale to accommodate an increasing number of devices, ensuring that your infrastructure can adapt to your evolving requirements.
Steps to Create a VPC for IoT Devices
Setting up a VPC involves the following steps:
- Select a cloud provider: Choose a cloud provider, such as AWS, Azure, or Google Cloud, that supports VPC creation.
- Define your network parameters: Define your network parameters, including IP ranges and subnets, to establish the structure of your VPC.
- Configure security groups and ACLs: Configure security groups and access control lists (ACLs) to restrict unauthorized access to your devices and data.
- Deploy your IoT devices: Deploy your IoT devices within the VPC and test connectivity to ensure proper functionality.
This is the place where your detailed information and table should be placed.
The Raspberry Pi, a versatile and cost-effective single-board computer, has emerged as a valuable tool for IoT projects, particularly for establishing secure connections between devices and a VPC. Its compatibility with various operating systems and programming languages makes it an ideal platform for configuring secure communication channels. The Raspberry Pi's flexibility allows developers to tailor the system to specific needs, making it suitable for a wide range of applications, from home automation to industrial monitoring.
Why Use Raspberry Pi for IoT?
Raspberry Pi is a versatile, low-cost device that serves as an excellent platform for IoT projects. Its affordability, compact size, and compatibility with various operating systems and programming languages make it an ideal choice for setting up secure connections between IoT devices and a VPC. It offers a balance of power, flexibility, and ease of use, making it suitable for both hobbyists and professionals.
Setting Up Raspberry Pi for IoT
Here's how you can configure a Raspberry Pi for secure IoT connections:
- Install an operating system: Install an operating system, such as Raspbian or Ubuntu, on your Raspberry Pi.
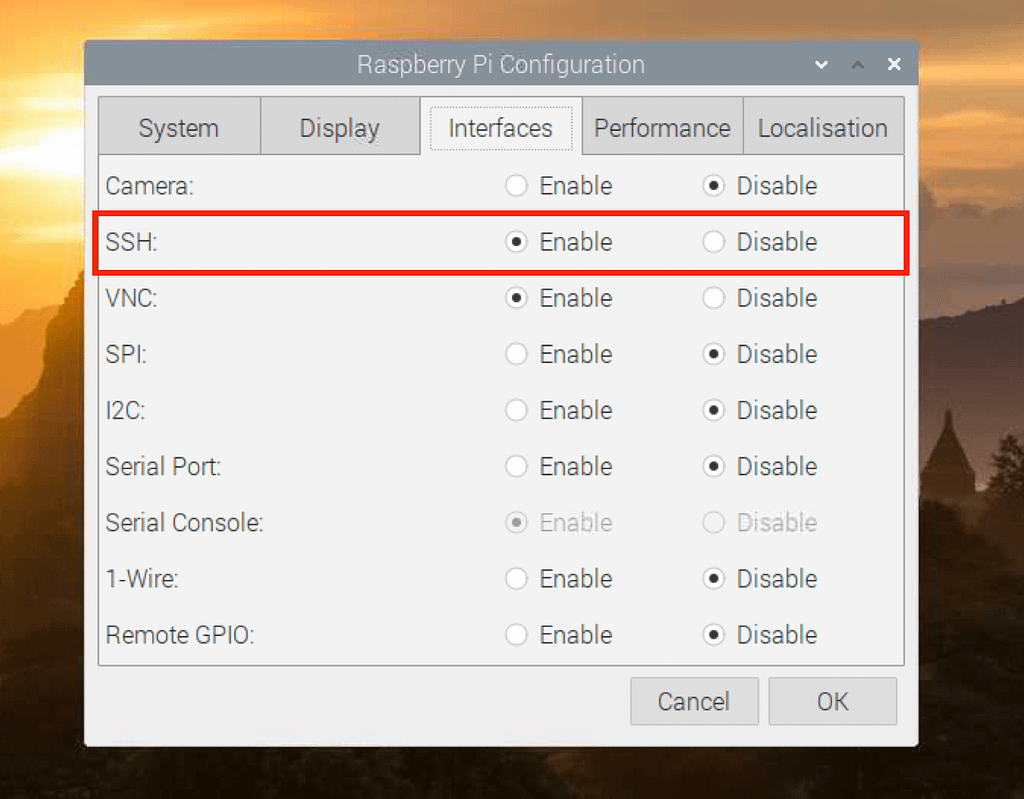
- Configure SSH: Configure SSH (Secure Shell) for remote access, ensuring it is secured with strong authentication methods, such as key-based authentication.
- Install necessary software packages: Install essential software packages, such as MQTT brokers (e.g., Mosquitto), SSL/TLS libraries (e.g., OpenSSL), and any other required dependencies, to facilitate secure communication.
- Test the connection: Test the connection between your Raspberry Pi and IoT devices to ensure proper functionality and data transmission.
Securing Raspberry Pi for IoT Deployments
To ensure the security of your Raspberry Pi in an IoT environment, consider the following best practices:
- Change default passwords: Change the default passwords and use strong, unique credentials for all user accounts and services.
- Regularly update the operating system: Regularly update the operating system and installed software to patch vulnerabilities and mitigate potential security risks.
- Implement firewalls and intrusion detection systems: Implement firewalls and intrusion detection systems to monitor and block suspicious activities, protecting your network from unauthorized access and malicious attacks.
This is the place where your detailed information and table should be placed.
Access to free and readily available resources is essential for establishing secure IoT connections. Several tools and libraries are available at no cost, enabling you to implement robust security measures without incurring significant expenses. These resources encompass a wide range of capabilities, including secure communication protocols, encryption, and network monitoring, empowering you to build a secure and resilient IoT infrastructure.
Where to Find Free Tools
Several free tools and resources are available to help you securely connect remote IoT devices to a VPC using a Raspberry Pi. Some popular options include:
- MQTT Brokers: Mosquitto and HiveMQ offer free versions for small-scale deployments, providing a lightweight and efficient messaging protocol for IoT devices.
- Encryption Libraries: OpenSSL and GnuTLS provide robust encryption capabilities, enabling you to protect data transmission and ensure confidentiality.
- Network Monitoring Tools: Wireshark and Nmap can help you identify and mitigate potential security threats, by providing valuable insights into network traffic and vulnerabilities.
How to Choose the Right Tool
When selecting free tools for your IoT project, consider the following factors:
- Compatibility: Ensure that the tools are compatible with your Raspberry Pi and IoT devices, as well as your chosen operating system.
- Ease of installation and configuration: Choose tools that are easy to install and configure, and provide clear documentation and support resources.
- Community support and available documentation: Prioritize tools with active communities and comprehensive documentation, to facilitate troubleshooting and ensure ongoing support.
Best Practices for Using Free Tools
To maximize the effectiveness of free tools in securing your IoT environment:
- Regularly update tools: Regularly update the tools to ensure they have the latest security patches and address any known vulnerabilities.
- Document your configurations: Document your configurations and settings for future reference, enabling you to replicate and troubleshoot your setup.
- Test tools in a controlled environment: Test the tools in a controlled environment before deploying them in a production setting, to identify and resolve any potential issues.
This is the place where your detailed information and table should be placed.
Implementing secure communication protocols is fundamental to protecting the data exchanged between IoT devices and a VPC. Secure protocols ensure the confidentiality, integrity, and authenticity of the data, minimizing the risk of unauthorized access and malicious attacks. Choosing the appropriate protocol and configuring it correctly are crucial steps in establishing a secure and reliable IoT infrastructure.
Overview of Communication Protocols
Secure communication protocols are essential for protecting data transmitted between IoT devices and a VPC. Common protocols include:
- MQTT (Message Queuing Telemetry Transport): A lightweight protocol that is ideal for resource-constrained devices, providing efficient data transmission over low-bandwidth networks.
- CoAP (Constrained Application Protocol): Designed for low-power and low-bandwidth networks, CoAP offers a simplified communication framework suitable for devices with limited resources.
- HTTPS: Provides secure web communication using SSL/TLS encryption, ensuring the confidentiality and integrity of data exchanged between devices and servers.
Configuring MQTT for Secure IoT Connections
To configure MQTT for secure communication:
- Install an MQTT broker: Install an MQTT broker, such as Mosquitto, on your Raspberry Pi or a cloud-based server.
- Enable SSL/TLS encryption: Enable SSL/TLS encryption to secure data transmission, protecting the data from eavesdropping and unauthorized access.
- Set up username and password authentication: Set up username and password authentication for authorized access, ensuring that only authenticated devices can connect to the broker and publish/subscribe to topics.
Ensuring Data Integrity
Data integrity is critical in IoT environments. To ensure data remains unaltered during transmission:
- Use digital signatures: Use digital signatures to verify the authenticity of data, ensuring that the data originates from a trusted source and has not been tampered with during transit.
- Implement checksums: Implement checksums to detect and correct errors, ensuring that the data is transmitted accurately and reliably.
- Regularly audit logs: Regularly audit logs to identify and address any discrepancies, monitoring the activity of devices and detecting potential security incidents.
This is the place where your detailed information and table should be placed.
Establishing and maintaining a secure IoT VPC connection demands the implementation of robust security practices. These practices encompass network segmentation, regular security audits, and employee training, working together to reduce the risk of breaches and ensure the ongoing integrity of your IoT infrastructure. These strategies are essential to mitigate the impact of potential threats and protect your systems from unauthorized access.
Network Segmentation
Segmenting your network ensures that IoT devices are isolated from other systems, reducing the risk of lateral movement in case of a breach. Use VLANs or subnets to create distinct network zones for your IoT devices, limiting the impact of a compromised device.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and ensures compliance with security standards. Automate audits using tools like Nessus or OpenVAS to streamline the process, ensuring ongoing security assessment.
Employee Training and Awareness
Human error is a significant factor in security breaches. Educate your team about IoT security best practices and encourage them to report any suspicious activities promptly, fostering a culture of security awareness.
This is the place where your detailed information and table should be placed.
The landscape of IoT security is continually evolving, with emerging technologies and changing regulations shaping the future of secure IoT deployments. Understanding these trends is essential for proactively addressing potential threats and maintaining the integrity of your IoT systems. Staying ahead of the curve requires a commitment to continuous learning and adaptation.
Emerging Technologies
Several emerging technologies are shaping the future of IoT security:
- Blockchain: Provides decentralized and tamper-proof data storage, enhancing the security and integrity of data.
- AI and Machine Learning: Enhance threat detection and response capabilities, allowing for more proactive and intelligent security measures.
- Quantum Cryptography: Offers unparalleled encryption strength for secure communications, addressing the increasing sophistication of cyberattacks.
Regulatory Landscape
As IoT adoption grows, governments and organizations are developing regulations to ensure data privacy and security. Staying informed about these regulations is crucial for maintaining compliance, as compliance requirements are increasingly strict.
Adapting to New Challenges
The evolving threat landscape requires continuous adaptation. Stay updated with the latest security trends and invest in tools and training to address emerging challenges, ensuring the long-term security of your systems.
This is the place where your detailed information and table should be placed.

Detail Author:
- Name : Mathew Ankunding
- Username : mhomenick
- Email : ole.walsh@yahoo.com
- Birthdate : 1983-10-23
- Address : 234 Gaylord Branch Vernieberg, WA 38970-3020
- Phone : (918) 704-2867
- Company : Dach, Ondricka and Keebler
- Job : Graduate Teaching Assistant
- Bio : Facilis minus aliquid cumque quis officia. Atque amet quisquam ipsum est. Libero et nostrum qui accusantium est laboriosam. Et est qui vero corrupti assumenda dolorem.
Socials
linkedin:
- url : https://linkedin.com/in/katarina_real
- username : katarina_real
- bio : Ea pariatur aliquid tenetur rerum voluptas ad.
- followers : 843
- following : 660
tiktok:
- url : https://tiktok.com/@kub2014
- username : kub2014
- bio : In quos modi temporibus pariatur.
- followers : 3505
- following : 2166
instagram:
- url : https://instagram.com/kkub
- username : kkub
- bio : Et maiores maiores modi qui animi debitis eos. Eius quas quisquam accusantium voluptas et qui.
- followers : 2976
- following : 1903