Secure RemoteIoT Access With SSH: A Complete Tutorial
Are you looking for a way to remotely and securely manage your Internet of Things (IoT) devices? The ability to securely connect to and control these devices from afar is no longer a luxury; it's a necessity for anyone involved in modern technology.
The widespread adoption of IoT devices across various sectors, from manufacturing and healthcare to smart homes and environmental monitoring, has created an urgent need for secure remote access methods. Secure Shell (SSH) offers a robust and reliable solution to meet this demand. This guide delves into the practical aspects of using SSH for remote access to IoT devices, providing a clear path from initial setup to advanced configurations, all while emphasizing the importance of security in the digital age.
The world of RemoteIoT is vast and multifaceted, offering unique challenges and opportunities. From real-time data monitoring and automated system updates to remote diagnostics and integration with cloud platforms, the capabilities are extensive. However, this also brings forth the need for a secure, reliable and versatile method of access. The content below will delve into how to establish SSH connections, troubleshoot common issues, and optimize your IoT network. Let's embark on this journey!
- Unveiling Sexy Open Trends Impact Amp Future Google Discover
- Urban Air Crystal Lake Fun Fitness Thrills
Below is a table summarizing the main components of a secure RemoteIoT device SSH connection.
| Component | Description | Importance |
|---|---|---|
| SSH Client | Software used to initiate and manage SSH connections (e.g., PuTTY, OpenSSH). | Enables secure communication with the RemoteIoT device. |
| Device IP Address | The unique network identifier of the RemoteIoT device. | Specifies the target device for the SSH connection. |
| Login Credentials | Username and password (or SSH key) required for authentication. | Verifies the user's identity and grants access to the device. |
| Network Connection | A stable internet connection between the client and the RemoteIoT device. | Ensures reliable data transmission and remote access. |
| Firewall Configuration | Rules that allow or deny SSH traffic (typically on port 22). | Controls access to the RemoteIoT device and enhances security. |
Reference: Example Website
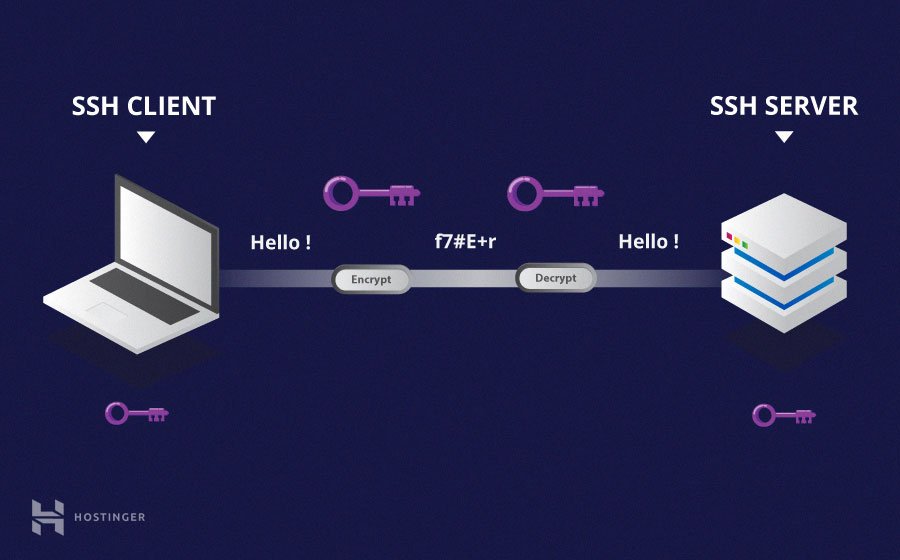
At its core, SSH, or Secure Shell, is a cryptographic network protocol. It acts as a secure conduit for data transmission, facilitating remote command execution and providing a range of secure network services. Its primary function is to establish a secure channel over an unsecured network by encrypting all data that travels through it.
The benefits of using SSH are many, and particularly relevant to the challenges of securing IoT devices. SSH offers robust data encryption, which prevents eavesdropping and data breaches. It provides authentication mechanisms to verify the identity of users attempting to connect. It supports file transfer, enabling secure exchange of files between the client and the device. By using SSH in the context of RemoteIoT devices, you are guaranteed that your connection is secure and prevents unauthorized access and potential data breaches.
Before beginning the process of establishing an SSH connection, certain prerequisites are essential. These can be broadly classified into hardware and software requirements. A thorough understanding of these requirements will ensure a smooth and efficient setup.
On the hardware side, the primary requirement is a computer or laptop capable of running an SSH client. It is also imperative that this computer has a stable and reliable internet connection. Finally, the RemoteIoT device itself must be SSH-enabled, a characteristic commonly supported by modern devices designed for remote management.
The software requirements center around the SSH client. For Windows users, a popular choice is PuTTY, a free and widely used SSH and Telnet client. Alternatively, Linux and Mac users can utilize the built-in OpenSSH client. The second key requirement is the access credentials for the RemoteIoT device, typically the IP address and login information (username and password), obtained from the device documentation or the network administrator.
The following is a step-by-step tutorial for establishing an SSH connection to your RemoteIoT device.
The initial step involves installing an SSH client. For Windows, PuTTY is a reliable choice, while Linux and Mac users often leverage the native OpenSSH client, which is typically pre-installed. The SSH client will serve as the primary interface for initiating and managing your secure connection.
The second step is gathering device information. Crucial elements are the IP address and the login credentials for your RemoteIoT device. This information can often be found within the device documentation or provided by the network administrator. The IP address is the device's unique identifier on the network, and the login credentials are required to authenticate your access.
Next, the connection must be established. Open the SSH client and input the IP address of the RemoteIoT device. Subsequently, authenticate yourself using the provided credentials. Upon successful authentication, a secure connection is established, enabling remote access to the device.
The final step is to verify the connection. Once you have established a connection, verify that you have access to the device's command-line interface. This check confirms the stability and functionality of the connection. Successful access to the command-line interface means you can now securely manage and monitor your RemoteIoT device.
While establishing an SSH connection, you may face certain challenges. Familiarity with these common issues and corresponding troubleshooting techniques is critical for a successful and efficient setup.
A common issue is the "Connection Refused" error. This typically indicates that the RemoteIoT device's SSH service is not running, or that a firewall is blocking incoming connections on port 22, the default SSH port. Verifying the service status and firewall configuration is essential to resolve this problem.
Another frequent problem is authentication failure. This usually indicates incorrect login credentials. Double-check the credentials and ensure they are entered correctly. Additionally, if key-based authentication is being used, verify that the SSH keys are properly configured. Incorrectly configured keys can also lead to authentication failure.
Network connectivity issues can also prevent an SSH connection. A stable internet connection is a prerequisite. Ensure that the internet connection is active and functioning. Verify that the device's IP address is accurate and reachable. If the device cannot be reached via its IP, the connection will fail.
Security is paramount when dealing with remote access to IoT devices. The following security best practices should be implemented to ensure that SSH connections are secure and protected from potential threats.
Strong passwords are the first line of defense. Use unique, strong passwords that are not easily guessable or based on default credentials. The strength of your passwords is directly proportional to the security of your system.
Key-based authentication adds an additional layer of security. This approach eliminates the need for passwords, using cryptographic keys for authentication instead. Key-based authentication is significantly more secure than password-based authentication and should be enabled whenever possible.
Limiting access is also important. Restrict SSH access to trusted IP addresses to minimize the risk of unauthorized connections. Disable root login, if possible, to prevent attackers from directly accessing the root account, further securing the system.
Beyond the basics, advanced configurations can optimize your RemoteIoT device's performance and security. These configurations can enhance the functionality and safety of your remote access setup.
Port forwarding allows external access to your RemoteIoT device. Setting up port forwarding on your router creates a secure channel for remote access from outside your local network. This must be implemented with careful consideration to network security.
SSH tunneling can be used to securely access services running on the RemoteIoT device, such as databases or web servers. This method encrypts the traffic, ensuring that sensitive data is protected during transit. Tunneling is particularly useful when accessing services that are not directly exposed to the internet.
Automated backups are a crucial measure for ensuring that your device's data is regularly saved. This allows you to restore your data in case of failure or data loss. Regular backups are a preventative measure that can minimize downtime and protect your valuable data.
Several tools and software can enhance the experience when working with RemoteIoT devices over SSH. These tools can simplify and improve the management and monitoring of your devices.
Popular SSH clients include PuTTY for Windows and OpenSSH for Linux/Mac. These are the primary tools for establishing and managing SSH connections. Having a reliable SSH client is fundamental for remote access.
Monitoring tools such as Netdata and Prometheus offer valuable insights into your device's performance. These tools provide metrics and data that can help you identify potential issues and optimize the performance of your devices. They are essential for maintaining the health and efficiency of your IoT network.
SSH is versatile and applicable to various use cases in the context of RemoteIoT devices. Its adaptability makes it a core technology across different industries.
Industrial automation benefits significantly from SSH. It allows remote monitoring and control of industrial equipment, helping ensure optimal performance and minimizing downtime. This improves the efficiency and productivity of industrial processes.
In smart home systems, SSH enables remote access and management of devices such as thermostats and security systems. This remote control functionality enhances convenience and security, allowing users to manage their homes from anywhere in the world.
SSH also plays a vital role in environmental monitoring, facilitating the collection and analysis of data from sensors deployed in remote locations. The data obtained provides valuable insights for environmental research, helping to understand and manage environmental conditions more effectively.
As technology evolves, the role of SSH in securing IoT devices will become even more critical. The future holds many exciting trends that will shape how SSH is used in the IoT landscape.
Quantum-resistant encryption is a key development. As quantum computing technology advances, traditional encryption methods are at risk. Quantum-resistant encryption ensures long-term security for IoT devices, protecting them from future threats.
AI-driven security will be crucial in detecting and responding to security threats in real-time. AI can analyze network traffic and identify malicious activities. This will significantly enhance the protection of IoT networks.
The expansion of 5G connectivity will improve the performance and reliability of remote IoT connections. Increased bandwidth and reduced latency will enhance the user experience and enable more complex IoT applications.

Detail Author:
- Name : Henderson Schoen
- Username : prosacco.naomie
- Email : lupe.predovic@kihn.com
- Birthdate : 1980-02-22
- Address : 355 Nicolas Forest Kozeyland, WA 64497-6653
- Phone : 1-651-840-0593
- Company : Conn-Treutel
- Job : Nuclear Equipment Operation Technician
- Bio : Doloribus culpa saepe facilis nesciunt vel quia. Sed itaque sapiente ratione eum assumenda ut sit. Sequi id dolores et unde sit.
Socials
facebook:
- url : https://facebook.com/arlo_official
- username : arlo_official
- bio : Iure ut modi harum. Fugit cumque dolore eligendi.
- followers : 6573
- following : 1389
linkedin:
- url : https://linkedin.com/in/arlo.jerde
- username : arlo.jerde
- bio : Sunt neque optio natus dolore voluptates.
- followers : 434
- following : 323
instagram:
- url : https://instagram.com/arlojerde
- username : arlojerde
- bio : Rem sit nihil sunt sunt in a iste. Id reiciendis repellendus ut.
- followers : 3596
- following : 2344
twitter:
- url : https://twitter.com/arlojerde
- username : arlojerde
- bio : Possimus laudantium et quam ut quae. Et ut excepturi dolores numquam. Tempora quia doloremque expedita qui eveniet.
- followers : 6318
- following : 2146