SSH To IoT Devices: Secure Remote Access Guide
Is securing your remote IoT devices a constant worry? In today's rapidly evolving technological landscape, ensuring the integrity and confidentiality of communication channels is no longer a luxury but a necessity.
The relentless expansion of the Internet of Things (IoT) has presented organizations with the formidable challenge of managing and safeguarding a vast network of remote devices. Secure Shell (SSH) emerges as a crucial tool, offering a secure and reliable protocol for establishing encrypted communication between these devices. This article serves as a comprehensive guide, designed to illuminate the process of setting up and effectively utilizing SSH for the management of remote IoT devices.
Secure Shell (SSH)
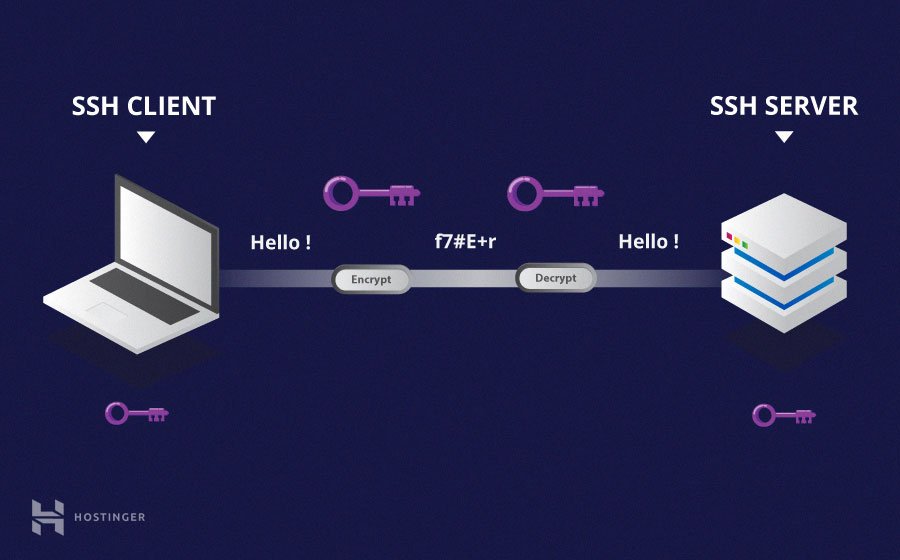
SSH, or Secure Shell, functions as a network protocol, enabling secure communication between devices across potentially unsecured networks. Its primary role is to establish a protected channel for remote access to servers, routers, and, crucially, IoT devices. By employing encryption for data transmission, SSH guarantees confidentiality, integrity, and authentication throughout the communication process.
- 9inch Pizza Craze Why This Size Is Your Next Favorite Bite
- Is Gunther Eagleman Real Unveiling The Mystery
Operating by default on port 22, SSH presents a significantly more secure alternative to older, less protected protocols such as Telnet and FTP. Its widespread support across various operating systems, including Linux, macOS, and Windows, contributes to its versatility across a broad spectrum of applications.
In the context of IoT devices, SSH assumes a vital role in the secure management and maintenance of remote systems. Whether your tasks involve configuring sensors, monitoring environmental conditions, or performing firmware updates, SSH ensures that all interactions with IoT devices are shielded from unauthorized access and potential data breaches.
The Strategic Advantages of Using SSH for IoT Devices
The utilization of SSH for IoT devices offers a variety of compelling advantages when compared to alternative communication protocols. Here are some key benefits that highlight why SSH is the preferred choice for securing IoT connections:
- Discover Grow With Ubetteme Your Path To Selfimprovement
- New Hope For Gums Independence Mo Gum Regeneration
- Encryption: SSH encrypts all data transmitted between devices, effectively preventing eavesdropping and data tampering. This ensures that sensitive information remains protected during transit.
- Authentication: SSH provides robust authentication mechanisms, supporting multiple methods, including password-based and public-key authentication. This safeguards access, ensuring only authorized users can connect to and manage the device.
- Compatibility: SSH demonstrates wide compatibility with a variety of IoT platforms and operating systems. This characteristic ensures that SSH can be readily integrated into existing systems, facilitating seamless adoption.
- Reliability: SSH connections are engineered to be reliable and robust, even when operating in environments characterized by unstable network conditions. This ensures that remote management and data transfer remain consistent and dependable.
These features make SSH an ideal solution for securing IoT devices, especially when deployed in remote or untrusted locations, where maintaining secure communication is paramount.
Table
This table summarizes the key advantages of using SSH for IoT devices. It highlights the security and reliability features of SSH, and how it can improve the management of your IoT devices.
| Feature | Benefit |
|---|---|
| Data Encryption | Protects sensitive data during transmission, preventing eavesdropping and tampering. |
| Strong Authentication | Ensures only authorized users can access and control the IoT device, improving security posture. |
| Platform Compatibility | Supports a wide range of IoT platforms and operating systems, for ease of integration. |
| Reliable Connections | Provides stable and consistent connections, regardless of network conditions. |
| Remote Management | Securely manage and control IoT devices from anywhere with network access. |
For more detailed information, please refer to IETF RFC 4251, which outlines the SSH protocol in detail.
Essential Prerequisites
Hardware and Software
Before you embark on the process of setting up SSH for your IoT device, it is essential to ensure that you have the necessary hardware and software components in place.
Hardware Prerequisites
To successfully establish an SSH connection to your IoT device, you must have the following hardware components:
- An IoT device that operates on an SSH-capable operating system (e.g., Raspberry Pi, ESP32 running a Linux distribution).
- A stable internet connection or a reliable local network connection.
- A computer or laptop equipped with an SSH client. Examples of such clients include PuTTY for Windows and Terminal (or similar) for macOS and Linux.
Software Prerequisites
In addition to the hardware requirements, you'll need the following software:
- An SSH server that is installed and configured on your IoT device. The most common example is OpenSSH.
- An SSH client installed on your local machine.
- A basic, functional understanding of command-line operations. This will be essential for interacting with the device via SSH.
Ensuring that you have these prerequisites prepared will significantly streamline the setup process, allowing you to establish secure remote access to your IoT device with minimal issues.
Step-by-Step
The process of setting up an SSH server on your IoT device requires several distinct steps. Detailed below is a comprehensive guide to walk you through the entire setup process.
Step 1
The procedure for enabling SSH might vary depending on the specific operating system installed on your IoT device. For example, if you are using a Raspberry Pi running Raspbian, the steps are as follows:
- Open the Raspberry Pi Configuration tool. This is typically done by typing `sudo raspi-config` in the terminal.
- Navigate to the "Interfacing Options" menu and enable the SSH service.
- Reboot your device to ensure that the changes are applied and the SSH service is active.
Step 2
If your IoT device does not have an SSH server installed, you can readily install OpenSSH using the following command. Run this command within the terminal on your device:
sudo apt update && sudo apt install openssh-server
This command will update the package lists and install the necessary packages required to enable SSH functionality on your device. Ensure your device has an active internet connection when running this command to download the required components.
Step 3
After installing the SSH server, you have the option to customize its settings by modifying the configuration file. The configuration file is located at:
sudo nano /etc/ssh/sshd_config
Here are some common configurations that you might want to consider:
- Changing the default SSH port. For security purposes, consider changing the default port (22) to a custom port.
- For enhanced security, disable password authentication and enable public-key authentication. This enhances security by reducing the risk of brute-force attacks.
Establishing the Connection
Once the SSH server is properly set up on your IoT device, you're ready to connect to it remotely using an SSH client. Here's a detailed guide to help you through the connection process.
Step 1
The initial step involves identifying the IP address assigned to your IoT device. You can obtain the IP address by running the following command within the terminal on your device:
hostname -I
This command will display the IP address associated with your device on the network.
Step 2
On your local machine, open your preferred SSH client. Then, enter the following command, substituting the appropriate values:
ssh username@device_ip_address
Replace "username" with the exact username of a valid user account on your IoT device. Replace "device_ip_address" with the IP address you obtained in the previous step.
Table
A concise overview of the essential commands used to establish and manage SSH connections. This table will help you quickly reference the commands you need.
| Command | Description | Example |
|---|---|---|
| `hostname -I` | Displays the device's IP address | `hostname -I` |
| `ssh username@device_ip_address` | Connects to the remote device via SSH | `ssh pi@192.168.1.100` |
| `sudo apt update && sudo apt install openssh-server` | Installs the OpenSSH server | `sudo apt update && sudo apt install openssh-server` |
| `sudo nano /etc/ssh/sshd_config` | Opens SSH server configuration file for editing | `sudo nano /etc/ssh/sshd_config` |
Upholding Security
Although SSH provides a secure channel for communication, it is crucial to adhere to a set of best practices to further enhance its security. These practices will significantly fortify your IoT devices against unauthorized access.
- Use Strong, Unique Passwords: It is crucial to avoid using weak or easily guessable passwords for any SSH accounts. Instead, opt for strong, unique passwords that incorporate a combination of uppercase and lowercase letters, numbers, and symbols.
- Implement Public-Key Authentication: Whenever possible, disable password-based authentication and enable public-key authentication. This greatly improves security by employing cryptographic keys for authentication, significantly reducing the risk of brute-force password attacks.
- Modify the Default Port: To minimize the risk of automated attacks, change the default SSH port (22) to a custom port. This will make it more difficult for automated bots to identify your SSH server.
- Restrict User Access: Limit SSH access to specific users or groups. This can be achieved by configuring your SSH server to allow only certain users to connect, thereby reducing the potential attack surface.
By implementing these practices, you will significantly protect your IoT devices from unauthorized access and potential cyber threats, thereby maintaining the integrity of your systems.
Tackling the Challenges
At times, you might encounter issues when attempting to connect to your IoT device via SSH. The following outlines some of the common problems and their solutions.
- Connection Refused: If you get a "connection refused" error, ensure that the SSH server is running correctly on the IoT device. Also, verify that your device's firewall allows SSH traffic on the correct port (typically port 22 or the custom port you have configured).
- Incorrect Credentials: Double-check the username and password or the public key that you are using for authentication. Ensure that you are entering the correct credentials associated with an authorized user account.
- Network Issues: Verify your device's network connection. Make sure that it has a valid IP address and that the network connection is active and stable. Try pinging the device's IP address to check for basic network connectivity.
If the problem persists, consult the SSH server logs for more specific information about the cause of the issue. The server logs often provide valuable diagnostic details that can help in pinpointing the problem.
Exploring Advanced Capabilities
SSH offers a range of advanced features that can enhance its functionality for various IoT applications.
- Tunneling: Use SSH tunneling to establish secure connections to services running on your IoT device, such as web servers or databases. This feature encrypts the traffic, providing a secure channel for data transfer.
- Port Forwarding: Utilize port forwarding to forward specific ports from your local machine to the IoT device. This allows for remote access to services running on the device, enhancing accessibility and management capabilities.
- SSHFS: Employ SSHFS to mount remote file systems on your local machine. This feature offers seamless file management capabilities, allowing you to treat the remote file system as if it were local.
Exploring these features can unlock new possibilities for managing and interacting with your IoT devices, enhancing your remote control capabilities.
Leveraging Efficiency
Automating tasks with SSH significantly improves efficiency in managing IoT devices. The following outlines key automation techniques to consider:
- Scripting: Write scripts to automate routine tasks. Such scripts can be used to update firmware, collect sensor data, or perform other regularly needed operations.
- Cron Jobs: Schedule SSH commands to run at specific intervals using cron jobs. This allows you to automate regular maintenance tasks, such as system updates or data backups.
- Remote Monitoring: Use SSH to remotely monitor device performance and health metrics. This enables you to collect vital information on device operation and status.
By incorporating automation, you can streamline operations, reduce manual intervention, and improve the overall efficiency of managing your IoT infrastructure.

Detail Author:
- Name : Lula Von MD
- Username : roma19
- Email : ekunze@reilly.org
- Birthdate : 2001-07-19
- Address : 13030 Bruen Plain Apt. 238 Beerton, CT 14170
- Phone : +1-908-432-3786
- Company : Grimes Ltd
- Job : Psychiatric Technician
- Bio : Eos earum autem eius. Voluptate sunt occaecati ipsam. Molestias excepturi dolor soluta sunt fugiat et.
Socials
instagram:
- url : https://instagram.com/bernita4264
- username : bernita4264
- bio : Iusto aut voluptates blanditiis repellendus. Hic nobis numquam dolores dolores quas.
- followers : 5995
- following : 297
tiktok:
- url : https://tiktok.com/@bernita2927
- username : bernita2927
- bio : Tempore nam expedita aut dignissimos. Vel minus ea provident molestiae.
- followers : 6262
- following : 1152
twitter:
- url : https://twitter.com/bstanton
- username : bstanton
- bio : Et debitis facere amet unde nobis quidem. Necessitatibus praesentium laudantium in. Praesentium eaque nemo optio dolores. Quia ea nihil tenetur.
- followers : 6141
- following : 2478
linkedin:
- url : https://linkedin.com/in/bernita_id
- username : bernita_id
- bio : Nam nulla explicabo eaque officiis deleniti enim.
- followers : 3012
- following : 414
facebook:
- url : https://facebook.com/bernita.stanton
- username : bernita.stanton
- bio : Ad quia ut in est iusto. Quis vitae beatae quos iusto.
- followers : 4859
- following : 1732