Unlock RemoteIoT: Securely Connecting Devices Behind Firewalls
Is your organization's digital future being held back by the invisible barrier of a firewall? It doesn't have to be. Effectively harnessing RemoteIoT technology behind a firewall is not just possible, it's essential for the innovation and efficiency that define the modern era.
The Internet of Things (IoT) has rapidly transformed industries, creating smart homes, connected manufacturing plants, and healthcare systems. However, a fundamental challenge has emerged: how to ensure secure and efficient connectivity for IoT devices operating behind firewalls. This article delves into the strategies and techniques necessary to successfully implement RemoteIoT, providing a comprehensive guide to navigating the complexities of network security while unlocking the full potential of your connected devices.
| Category | Details |
|---|---|
| Core Concept | RemoteIoT allows remote access and management of IoT devices, even when they are behind firewalls. |
| Key Technologies Involved |
|
| Main Challenges |
|
| Solutions and Best Practices |
|
| Implementation Steps |
|
| Common Troubleshooting Issues |
|
| Future Trends |
|
| Relevant URL Reference | Example IoT Website - RemoteIoT and Firewalls |
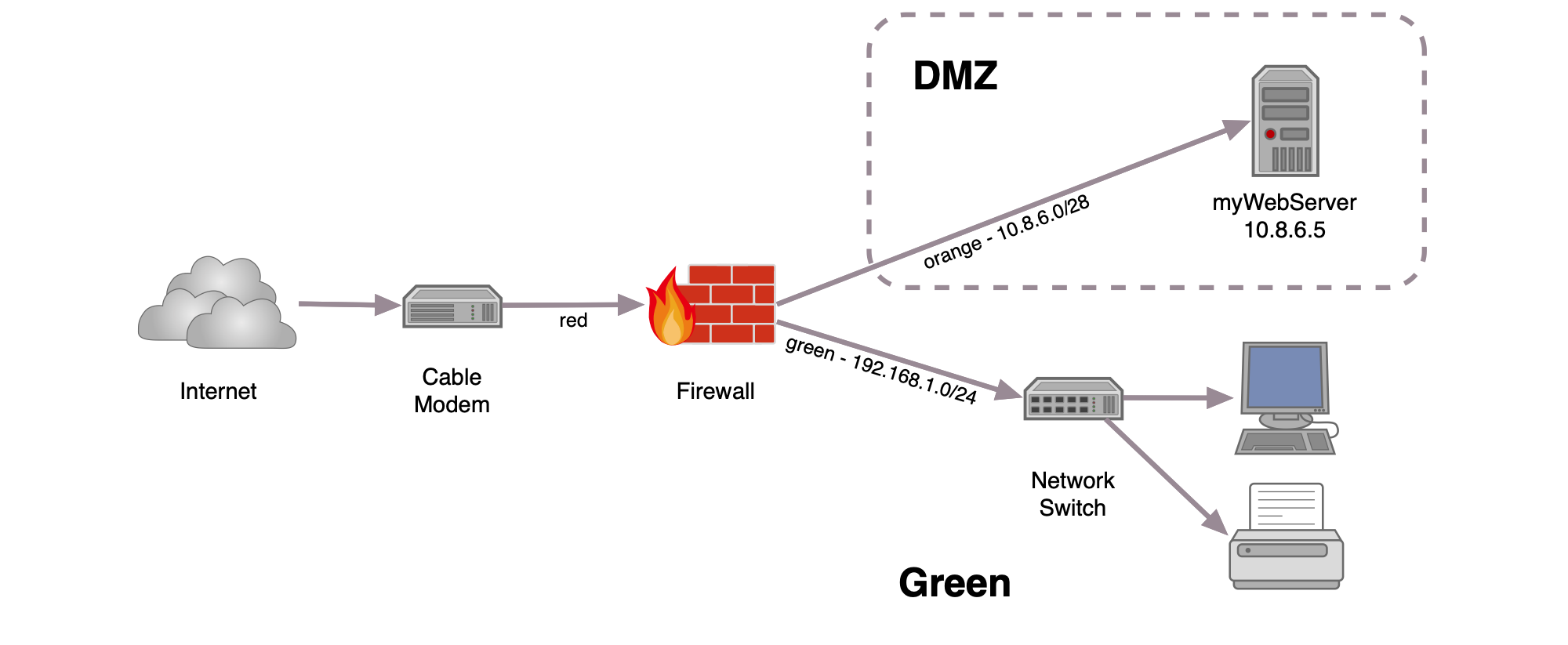
The very nature of firewalls, designed to protect networks from unauthorized access, inherently presents a hurdle for RemoteIoT applications. These firewalls meticulously examine incoming and outgoing network traffic based on pre-defined security rules, acting as a vital safeguard against potential threats. However, this protective mechanism can inadvertently impede the smooth flow of data between IoT devices and external systems.
- Lakers Roster 202324 Season Breakdown Key Players
- Dive Deep Into Sexy Filmen Exploring Sensuality Cinema
Firewalls themselves are not monolithic entities; they come in various forms, each employing different methods to secure networks. Packet filtering firewalls, operating at the network layer, analyze individual data packets, allowing or denying them based on established rules. Stateful inspection firewalls go a step further, tracking active connections and assessing packets in the context of their connection state. Application-level gateways, residing at the application layer, provide advanced filtering capabilities, scrutinizing the content of data streams. Understanding these nuances in firewall types is paramount when deploying RemoteIoT, as the choice of firewall and its configuration directly impacts device connectivity and data transmission.
RemoteIoT technology forms the backbone of many modern advancements, enabling the remote access and management of devices regardless of their physical location. This technology seamlessly facilitates interaction between devices and centralized systems. These solutions depend on cloud-based platforms, application programming interfaces (APIs), and secure communication protocols.
The capabilities of RemoteIoT extend far beyond mere access. Key features include secure data encryption, ensuring that sensitive information remains confidential during transit. Real-time monitoring and control empower users to proactively manage their devices, responding instantly to any issues or changes. The inherent scalability of RemoteIoT allows for effortless expansion, accommodating deployments of any size. Furthermore, RemoteIoT seamlessly integrates with existing IoT ecosystems, creating a unified and efficient management system.
- Lakers Roster 2023 Analysis Game Highlights
- Hyungry Temporary Replacement 3 Your Guide To Smart Solutions
The successful implementation of RemoteIoT solutions encounters several challenges, primarily related to the inherent security and connectivity restrictions of firewalls. The primary function of firewallsto block unauthorized accesscan interfere with the smooth communication between IoT devices and external systems. The common challenges faced are:
- Network Restrictions: Firewalls frequently block specific ports and protocols, a crucial element of their security protocol, which inherently limits the connectivity of IoT devices.
- Latency Issues: The process of encrypting connections, while essential for security, may introduce delays that can negatively impact real-time data transmission.
- Security Concerns: Protecting data privacy and guarding against cyber threats are of paramount importance.
To successfully implement RemoteIoT behind a firewall, a strategic approach is necessary to mitigate the aforementioned challenges. Careful configuration and innovative solutions are key to ensuring uninterrupted communication and robust security. Here are some strategies that need to be considered.
1. Port Forwarding
Port forwarding offers a direct path for communication, allowing specific ports on a firewall to remain open, thus enabling smooth communication between IoT devices and external systems. However, this method demands meticulous configuration to ensure that only the necessary ports are exposed to the outside world, mitigating potential vulnerabilities.
2. Virtual Private Networks (VPNs)
VPNs provide a robust solution by establishing encrypted tunnels between devices and networks. This ensures secure communication, even when navigating behind firewalls. VPNs are widely adopted in enterprise environments, enabling secure remote access and promoting a robust security posture.
3. Cloud-Based Gateways
Cloud-based gateways act as intermediaries between IoT devices and external systems, bypassing the constraints imposed by firewalls while maintaining an essential layer of security. This method streamlines communication without compromising the safety of the network.
The deployment of RemoteIoT solutions benefits from a range of tools and software designed to facilitate secure and efficient operation behind firewalls. These tools incorporate functionalities such as device management, robust data encryption, and comprehensive network monitoring.
Some of the most commonly used options include:
- MQTT Broker: A lightweight messaging protocol specifically designed for IoT applications, MQTT Broker offers simplicity and efficiency in data transmission.
- OpenVPN: Known for its security, OpenVPN is a robust VPN solution that ensures secure remote access to your network, shielding against unauthorized intrusions.
- Node-RED: A visual programming tool. It is used for IoT device integration.
Selecting the most appropriate tools and software hinges on the specific requirements of each use case. Careful evaluation ensures optimal performance, seamless functionality, and robust security.
Security is an ongoing process, it needs to be a top priority. Implementing best practices can significantly mitigate the risk of cyberattacks and prevent data breaches. Here are some recommendations that need to be considered.
- Use Strong Authentication: Implement multi-factor authentication (MFA) to enhance security.
- Encrypt Data Transmission: Utilize secure protocols like TLS/SSL to encrypt all data transmissions.
- Regularly Update Firmware: Keep both IoT devices and associated software up-to-date with the latest security patches.
The design and maintenance of a robust network architecture are crucial for the successful deployment of RemoteIoT. Planning and configuring network components requires strategic thought to ensure optimal performance, as well as a comprehensive security posture. Key considerations include the following:
- Segmentation: Divide the network into smaller segments.
- Load Balancing: Distribute network traffic evenly.
- Monitoring and Logging: Implement monitoring tools.
Implementing RemoteIoT behind a firewall requires a systematic approach. Here are the steps that need to be considered.
Step 1
Thoroughly evaluate the existing network infrastructure, which includes the identification of potential challenges, such as firewall restrictions and bandwidth limitations. A complete and in-depth understanding of existing infrastructure will help in smooth implementation.
Step 2
Carefully adjust the firewall rules to allow the essential ports and protocols for the seamless and secure RemoteIoT communication. It is essential to strike a balance between allowing the necessary traffic and maintaining robust security.
Step 3
Integrate robust encryption, robust authentication protocols, and comprehensive monitoring tools to safeguard the network and ensure ongoing security. This holistic approach creates a protective shield around the network.
Despite meticulous planning, unforeseen issues can arise. Below are common problems and their corresponding solutions:
- Connection Failures: Verify the firewall rules to ensure that the required ports are open and accessible.
- Data Latency: Optimize network configurations and use efficient communication protocols to minimize delays.
- Security Alerts: Promptly investigate and resolve any security incidents that may occur to maintain the integrity of the system.
The field of RemoteIoT is evolving rapidly. Anticipating the future trends will help in utilizing the full potential of the technology. Here are some of the key areas of focus that need to be considered.
- AI-Powered Analytics: Enhance data processing capabilities with artificial intelligence for better decision-making.
- Edge Computing: Reduce latency.
- 5G Connectivity: Enable faster and more reliable communication.

Detail Author:
- Name : Mallory Boyle
- Username : owiegand
- Email : ervin.labadie@boyer.com
- Birthdate : 2002-12-25
- Address : 8549 Otha Mall Lake Daphney, LA 62644
- Phone : 1-469-912-1135
- Company : Fahey Inc
- Job : Data Processing Equipment Repairer
- Bio : Consequatur cupiditate in quod amet voluptatem aut. Id porro beatae cupiditate. Esse velit excepturi magnam officiis ipsum vel excepturi.
Socials
facebook:
- url : https://facebook.com/ophelia.kshlerin
- username : ophelia.kshlerin
- bio : Consequatur voluptatem quod omnis nulla qui voluptatem aut eum.
- followers : 3729
- following : 104
instagram:
- url : https://instagram.com/ophelia_xx
- username : ophelia_xx
- bio : Magnam mollitia ipsam neque accusamus ad. Velit ducimus quo ut ut voluptas nisi.
- followers : 6310
- following : 818
linkedin:
- url : https://linkedin.com/in/okshlerin
- username : okshlerin
- bio : Tempore qui iusto debitis exercitationem.
- followers : 5181
- following : 615